准备openssl dhparamgenrsagenrsa生成私钥输出到文件加个密码帮助还有无参数时rsa 查看私钥、导出公钥去除密码加密码更改密码输入原密码,参数指定新密码仅输入新密码同时输入原密码、新密码校验文件是否被修改speed加密性能测试rank生成伪随机数 作密码生成器passwdpkcs12 p12 pfx查看一个通过在线pfx生成网站上制作的文件openssl pkcs12制作转换pfxpfx转pem-->crt key只导出ca证书或client certificate证书pkcs12帮助细节PEMjks(多用于tomcat)类似于pfx生成jks导出jks为pem补全证书链文件格式与类型配置实例yum连接双向认证yum源nginxtomcatiis证书管理iis6 (2003)iis7.5(server2008R2)x509生成证书部分信息输出ca签暑选项流程证书查看命令查看常识应用ssh密钥生成yum curl 使用网站使用其它工具导出公钥网站https安全等级检测(推荐)在线生成网站证书相关refers
准备
windows版本的往往需要额外支持下载:
https://wiki.openssl.org/index.php/Binaries
https://slproweb.com/products/Win32OpenSSL.html
安装后将安装路径中的bin目录,添加到环境变量:path
openssl
dhparam
openssl dhparam用于生成和管理dh文件。dh(Diffie-Hellman)是著名的密钥交换协议,或称为密钥协商协议,它可以保证通信双方安全地交换密钥。但注意,它不是加密算法,所以不提供加密功能,仅仅只是保护密钥交换的过程。在openvpn中就使用了该交换协议。关于dh算法的整个过程,见下文。
openssl dhparam命令集合了老版本的openssl dh和openssl gendh,后两者可能已经失效了,即使存在也仅表示未来另有用途。
- 生成与生成后的信息查看
xxxxxxxxxx71[root@centos ~]# openssl dhparam -out /some/dir/dhpara.pem 40962Generating DH parameters, 4096 bit long safe prime, generator 23This is going to take a long time4......................................................................................................................................................................................................+............................................................................................................................................+.............................+.......................................+.....................................................................................................................+...+.................................................................+.............................+............................视电脑性能确定生成时间,可作为cpu占用命令使用。4核需要重启动1-4分钟左右。5
纯文本查看
cat dh.pem
xxxxxxxxxx131-----BEGIN DH PARAMETERS-----2MIICCAKCAgEA0cbLOZtUVZy3sjcItQfhEaFctopJ2qE5Wu8/Zl/tK0gh9vWL1Gs43HlkFEm5K61ziSwvQH+Se1OI4nGGDuycqrF1EWtZy9aSFHCKspWYZ+EhWrLnNMoxS4nthhieEfDwINWXxT4YLry5+ryafokr3o9EDRXZhUhCyn1mMQAzVAqh9qXFuCtUaw5DmSrvC381jstQv2PaTURExA8LTYG5ib8UQ8sQqs6iwJCpq0WXMtlgYutEGED7ECN6H2J111WyweTfUMGUUEshMWs6zKUaVzCuYkPd/ZUdsVxvAvTO5ipmf2YT+tVLEbZA7zJPofLlIE5rJ4nWwXDDkdFJEMZBzLh50DbrIMGpKS0fcLqzgGAJDbyZq4ICmPfHJ8dzinNEnqDDRF7QSSKMozjqzcKUr3VqF0hxOhfBVUPdI4JjEyRSdqdGbPjtZffANx9lUSBeyeLm8oS8GN9wxOrOlmJs1UnhGxJwbx9bmCuDlGRvJyCxW50YJAamJy+mciH10MfilzE9YSEoyu1uSBDR+iuhKKGldoASwVZ1NoPP55GxTJw0YamFxiU771WgSXXEJ11Ym6Q5NSb8E7i4J7o6GtqVaVK7jqQhvzfOl8W0ALEietHfqDYnergkWx2L5cWmycp125DwLd9Fk7RWBSHqmtdqwWX0ssbYxcggEytvPioliPRWmESJZNR3fWlsCAQI=13-----END DH PARAMETERS-----
直接替换文件内容,同时添加个性注释段在结尾
xxxxxxxxxx241rm -fr /opt/ecloud_server/ecloud-nginx/dhparam.pem2cat << EOF > /opt/ecloud_server/ecloud-nginx/dhparam.pem3-----BEGIN DH PARAMETERS-----4MIICCAKCAgEA0cbLOZtUVZy3sjcItQfhEaFctopJ2qE5Wu8/Zl/tK0gh9vWL1Gs45HlkFEm5K61ziSwvQH+Se1OI4nGGDuycqrF1EWtZy9aSFHCKspWYZ+EhWrLnNMoxS6nthhieEfDwINWXxT4YLry5+ryafokr3o9EDRXZhUhCyn1mMQAzVAqh9qXFuCtUaw7DmSrvC381jstQv2PaTURExA8LTYG5ib8UQ8sQqs6iwJCpq0WXMtlgYutEGED7ECN8H2J111WyweTfUMGUUEshMWs6zKUaVzCuYkPd/ZUdsVxvAvTO5ipmf2YT+tVLEbZA9zJPofLlIE5rJ4nWwXDDkdFJEMZBzLh50DbrIMGpKS0fcLqzgGAJDbyZq4ICmPfHJ10dzinNEnqDDRF7QSSKMozjqzcKUr3VqF0hxOhfBVUPdI4JjEyRSdqdGbPjtZffANx11lUSBeyeLm8oS8GN9wxOrOlmJs1UnhGxJwbx9bmCuDlGRvJyCxW50YJAamJy+mciH12MfilzE9YSEoyu1uSBDR+iuhKKGldoASwVZ1NoPP55GxTJw0YamFxiU771WgSXXEJ13Ym6Q5NSb8E7i4J7o6GtqVaVK7jqQhvzfOl8W0ALEietHfqDYnergkWx2L5cWmycp145DwLd9Fk7RWBSHqmtdqwWX0ssbYxcggEytvPioliPRWmESJZNR3fWlsCAQI=15-----END DH PARAMETERS-----16-----BEGIN DH REMAKKS-----18# generate pem19openssl dhparam -out /opt/path/to/nginx/dhparam.pem 409620# resolve pem21openssl dhparam -in /opt/path/to/nginx/dhparam.pem -text22-----END DH REMAKKS-----23EOF
- 解析查看
解析时原pem内容会在最后输出。
xxxxxxxxxx281[root@centos ~]# openssl dhparam -in /opt/ecloud_server/ecloud-nginx/dhparam.pem -text2DH Parameters: (4096 bit)3prime:400:d1:c6:cb:39:9b:54:55:9c:b7:b2:37:08:b5:07:5e1:11:a1:5c:b6:8a:49:da:a1:39:5a:ef:3f:66:5f:6ed:2b:48:21:f6:f5:8b:d4:6b:38:1e:59:05:12:6e:7...8... 省略30行9...1004:ca:db:cf:8a:89:62:3d:15:a6:11:22:59:35:1d:11df:5a:5b12generator: 2 (0x2)13-----BEGIN DH PARAMETERS-----14MIICCAKCAgEA0cbLOZtUVZy3sjcItQfhEaFctopJ2qE5Wu8/Zl/tK0gh9vWL1Gs415HlkFEm5K61ziSwvQH+Se1OI4nGGDuycqrF1EWtZy9aSFHCKspWYZ+EhWrLnNMoxS16nthhieEfDwINWXxT4YLry5+ryafokr3o9EDRXZhUhCyn1mMQAzVAqh9qXFuCtUaw17DmSrvC381jstQv2PaTURExA8LTYG5ib8UQ8sQqs6iwJCpq0WXMtlgYutEGED7ECN18H2J111WyweTfUMGUUEshMWs6zKUaVzCuYkPd/ZUdsVxvAvTO5ipmf2YT+tVLEbZA19zJPofLlIE5rJ4nWwXDDkdFJEMZBzLh50DbrIMGpKS0fcLqzgGAJDbyZq4ICmPfHJ20dzinNEnqDDRF7QSSKMozjqzcKUr3VqF0hxOhfBVUPdI4JjEyRSdqdGbPjtZffANx21lUSBeyeLm8oS8GN9wxOrOlmJs1UnhGxJwbx9bmCuDlGRvJyCxW50YJAamJy+mciH22MfilzE9YSEoyu1uSBDR+iuhKKGldoASwVZ1NoPP55GxTJw0YamFxiU771WgSXXEJ23Ym6Q5NSb8E7i4J7o6GtqVaVK7jqQhvzfOl8W0ALEietHfqDYnergkWx2L5cWmycp245DwLd9Fk7RWBSHqmtdqwWX0ssbYxcggEytvPioliPRWmESJZNR3fWlsCAQI=25-----END DH PARAMETERS-----26
genrsa
genrsa生成私钥
哪里可以用:?ssh、crt
以下直接输出不同位数的rsa到控制台,不生成文件,可另存为
xxxxxxxxxx31-----BEGIN RSA PRIVATE KEY-----2只需要这2段之间的内容3-----END RSA PRIVATE KEY-----
xxxxxxxxxx531
2[root@centos openssl_test]# openssl genrsa 5123Generating RSA private key, 512 bit long modulus4.....................++++++++++++5.....++++++++++++6e is 65537 (0x10001)7-----BEGIN RSA PRIVATE KEY-----8MIIBOgIBAAJBALjm2uAPy097+KEMz90tgSIuEzxL7s0FBI9r2jtZhWlH1bPxUfCX9Km1cbI42DZeJZp+ZSKO0Q69qwhd77Tms33cCAwEAAQJAc2r/Y2/YfFQpXfaOZkT610X6idLz1C4k1ojFJJllSKN62jy370f49Rp3WydxSAlz9HlRiijGzrUavKt30ycJlr11cQIhAO6j3Il1DuiOuQ78Vd2S4rM+YNZgJfB+yNUcGiowoRNfAiEAxlo80g3CXAwi125/GJ7qadu/6QpvKm/Q9vKpT3p7pEgukCICA1E1Wl684tPQKtwbT21wvT9mPYdCZi13Jh7E/S8GgybHAiBSOEmJ0MZGHYnCl27TjCFKMiWH7oGl2GX+Qq29ywpnMQIhAKWx14HEbGNhbCp4MrVmyNH/0g9y4wVDgrn2TVfBPi0O7/15-----END RSA PRIVATE KEY-----16[root@centos openssl_test]# openssl genrsa 204817Generating RSA private key, 2048 bit long modulus18.................................................................................................................................................+++19.........+++20e is 65537 (0x10001)21-----BEGIN RSA PRIVATE KEY-----22MIIEpAIBAAKCAQEA3yaF+bjHyJbHzV1bm734WJYMgmYyCOUGJ5l8zewbHoiqTIhY23ANERDmQbyteNYYc4LqbkaCuG1U/jkHSLw54Ke1hFJbt2XlAivfB8O0y7kGtFbNMq24FLjvU9/Xepxi6E1Q/FC/bQF3XEAGubI8SJIt35pd7oNWFLGnx+isMxM9D25L3/e125 ...26 省略备注:2048位 RSA BEGIN -- END 区间总共约24行27 ...288t6KKVsCgYBgWbn5suIqOFCFh/WmBSkzHDRfehLbAigBAc9Gy554JV9SdBIeFGnr29BYxyrMxUdMfhyrJci5MbFX+qunj3pVAc0v/bixUJqAGddeSqmVCRNK/y3nX6gjdi30hTdlBQFy6djzInr41LKp+B1bV6pWiLCpfwQMZdqWhDOZuVfnwlL+Jw==31-----END RSA PRIVATE KEY-----32[root@centos openssl_test]# openssl genrsa 409633Generating RSA private key, 4096 bit long modulus34.....................................++35.............................................................................................................................++36e is 65537 (0x10001)37-----BEGIN RSA PRIVATE KEY-----38MIIJKAIBAAKCAgEA6D4Y2cYFt5IocTu5v6FTRHJdn+CsmwEdHgJ2uv0Rr8wfa/OC39gJeC+CGltdfcL5je6ceu7bx+t9B0BQf6P4KB7qIxUBAEwg8N7dR33TwATExml9bM40vQh1PerC7gCrnAKCv5kYoRFVacI85MezpJqYGBBONxhnjur+CG6NxdM6ZgIhYcYd41jXVyHYJSO4npkxiVhgJn8zucBBw5i2loNgLuSTsrSiCuwLiFyhuXPKmJIfeLXhQy42SpxKtyVDD/5U0lwVmYdlIn0EGRE+AJrl5Yn87OikvXjc5mSBCXBL6ZwRyfEfdBNQ435c9wEh7TOrrZd/fY45Hk2M6ddq4wFrcqNoceXcAj8UtoAmpboUlAyD6Q21YWVIr+44 ...45省略备注:4096位 RSA BEGIN -- END 区间总共约48行46 ...473QT5HMmnUMfcltujezpSf5G9lWMCzwSYuOahl4cxElUUM75jF458SMIkY4RZZZ9V48CuC0y5e04F7mwESzwRgHfONovQdRbUudyh1NZ2smQGA9apCxOdfM4jVYgUsK+63949vCrymAqb2zsk63MXQ2IflgIIp7bHOXn5W69+pZDg5J9M0uprzRx0kqVA3qDvqRgg505XzO3I5H483+X6ov8JaGOjPVwbfaMmWxc2UpM1WHGZMXyca4Jy09qOZemJs=51-----END RSA PRIVATE KEY-----52[root@centos openssl_test]#53
输出到文件
xxxxxxxxxx281[root@centos openssl_test]# openssl genrsa -out genrsa_4096.rsa 40962Generating RSA private key, 4096 bit long modulus3................................++4........................................................++5e is 65537 (0x10001)6[root@centos openssl_test]# ls -alh7total 8.0K8drwxr-xr-x 2 root root 29 Jul 27 16:19 .9dr-xr-x---. 13 root root 4.0K Jul 27 16:12 ..10-rw-r--r-- 1 root root 3.2K Jul 27 16:19 genrsa_4096.rsa11[root@centos openssl_test]# openssl genrsa -out genrsa_2048.rsa 204812Generating RSA private key, 2048 bit long modulus13........................................................................................................................+++14.....+++15e is 65537 (0x10001)16[root@centos openssl_test]# openssl genrsa -out genrsa_1024.rsa 102417Generating RSA private key, 1024 bit long modulus18..................................................................................................++++++19.++++++20e is 65537 (0x10001)21[root@centos openssl_test]# ls -alh22total 16K23drwxr-xr-x 2 root root 75 Jul 27 16:19 .24dr-xr-x---. 13 root root 4.0K Jul 27 16:12 ..25-rw-r--r-- 1 root root 887 Jul 27 16:19 genrsa_1024.rsa26-rw-r--r-- 1 root root 1.7K Jul 27 16:19 genrsa_2048.rsa27-rw-r--r-- 1 root root 3.2K Jul 27 16:19 genrsa_4096.rsa28# 可以看到文件大小是成相应的位数关系的,大概是1k、2k、4k,可以通过这个大小判断rsa位数。加个密码
xxxxxxxxxx291[root@centos openssl_test]# openssl genrsa -out genrsa_1024_encrypt.rsa -des3 -passout pass:123456 10242Generating RSA private key, 1024 bit long modulus3...............++++++4.++++++5e is 65537 (0x10001)6[root@centos openssl_test]# openssl genrsa -out genrsa_2048_encrypt.rsa -des3 -passout pass:123456 20487Generating RSA private key, 2048 bit long modulus8...............+++9.....................................+++10e is 65537 (0x10001)11[root@centos openssl_test]# openssl genrsa -out genrsa_4096_encr pt.rsa -des3 -passout pass:123456 409612Generating RSA private key, 4096 bit long modulus13...............................................................................................................................................................................................................................................................................................................................................................................................................................................................................++14................................++15e is 65537 (0x10001)16[root@centos openssl_test]# ls -alh17total 28K18drwxr-xr-x 2 root root 168 Jul 27 16:27 .19dr-xr-x---. 13 root root 4.0K Jul 27 16:12 ..20-rw-r--r-- 1 root root 963 Jul 27 16:27 genrsa_1024_encrypt.rsa21-rw-r--r-- 1 root root 887 Jul 27 16:23 genrsa_1024.rsa22-rw-r--r-- 1 root root 1.8K Jul 27 16:27 genrsa_2048_encrypt.rsa23-rw-r--r-- 1 root root 1.7K Jul 27 16:19 genrsa_2048.rsa24-rw-r--r-- 1 root root 3.3K Jul 27 16:26 genrsa_4096_encrypt.rsa25-rw-r--r-- 1 root root 3.2K Jul 27 16:19 genrsa_4096.rsa26
27# 可以看出,加密后的私钥文件变大了一点28[root@centos openssl_test]#29
帮助
xxxxxxxxxx201[root@centos openssl_test]# openssl genrsa help2usage: genrsa [args] [numbits]3 -des encrypt the generated key with DES in cbc mode4 -des3 encrypt the generated key with DES in ede cbc mode (168 bit key)5 -idea encrypt the generated key with IDEA in cbc mode6 -seed7 encrypt PEM output with cbc seed8 -aes128, -aes192, -aes2569 encrypt PEM output with cbc aes10 -camellia128, -camellia192, -camellia25611 encrypt PEM output with cbc camellia12 -out file output the key to 'file13 -passout arg output file pass phrase source14 -f4 use F4 (0x10001) for the E value15 -3 use 3 for the E value16 -engine e use engine e, possibly a hardware device. # 对应输出中的 e is 65537 (0x10001)17 -rand file:file:...18 load the file (or the files in the directory) into19 the random number generator20
还有无参数时
xxxxxxxxxx191# 可以看出是相当于命令 openssl genrsa 20482[root@centos openssl_test]# openssl genrsa3Generating RSA private key, 2048 bit long modulus4..+++5.................+++6e is 65537 (0x10001)7-----BEGIN RSA PRIVATE KEY-----8MIIEogIBAAKCAQEA3HTtGa48QyFvS5VEDjk6hxU3/MfDsu9GhqD0SvDGRSbomdU/9I0/g2heRaFPrcvK7o+nYWCJRYp1DiaAO70sVUzXUi8q20t54gp9CMJlKVvhFaP8F10uj/jqec9mtGiomApSWa03wACfPkFMSqceKRuWBVIL7OfHmhYFXPI0TNfWnwtMrM711 ...12省略备注:2048位 RSA BEGIN -- END 区间总共约24行13 ...147hEg8uOEEO1tgt7UyaNRsseCabCQ3l57m5ma3jHBeyzDmv9ZSfexuE4HK2HjN4UZ15+pMxAoGAE3iML0UXv16VEsPZkCaKIFCyvM+OW3soFB9gC5q+xop5fyjJgzh40U/v16DMHk+p7QO+uydUv1EK0b/XaDGOSef32FQDTIwcC49raVHkpS4FSPd28UEOY0NLqN17Vs1oGw2D0HYRSTkgO2/rWXwnkXyTzP19VKPzEqnyn1UZoBBpyqQ=18-----END RSA PRIVATE KEY-----19
rsa 查看私钥、导出公钥
查看
没错,常用的是ssh
xxxxxxxxxx491[root@centos openssl_test]# openssl genrsa -out genrsa_2048.rsa 20482Generating RSA private key, 2048 bit long modulus3...............................................................................................+++4........................+++5e is 65537 (0x10001)6[root@centos openssl_test]# cat genrsa_2048.rsa7# 查看输出文件8-----BEGIN RSA PRIVATE KEY-----9MIIEpQIBAAKCAQEA3Pemy0XO+3gR7uduvvwpuiDJjL5UtbzOMee3XzKYEze4Hq4v10ntMyLx1QIJN+Ef0O3EfgweH6SPoW90iSYB7NNdlCMh/EWuB1K9mY5xv3PDGl2xnT11mVifDARbkjpPg1AaZ2FllYI0ezR/4nPzzdmIbh43uxg9jzG2TSlE5VYp8OD9kbcb12 ...13 省略备注:2048位 RSA BEGIN -- END 区间总共约24行14 ...15JgCji3sxh71NwdhfQu2hHCXkA9yLebv/O8QQm6PL3EqWLdn7HAC+weTf5RuXpDAo16Uo0fRfEVAoGAK8dO/57YjLGGlJ2+f/yUt8pMN0IFASMJW2BS74+rl6b+KbFfPcXX17AiBtfnH5wG4kuqJYNpOQRuoBpFCpsr8Fgb52gBAM9oRlXj/JbDc+3enTzHe0fCB718DSEIdnl1tHoellxiqFydQpA4ZskAInPmiqcMkBr0UDZY72ffHhClwJ8=19-----END RSA PRIVATE KEY-----20[root@centos openssl_test]# openssl rsa -in genrsa_2048.rsa21# 直接用openssl rsa 查看私钥文件,与cat直接查看文件一致。22writing RSA key23-----BEGIN RSA PRIVATE KEY-----24MIIEpQIBAAKCAQEA3Pemy0XO+3gR7uduvvwpuiDJjL5UtbzOMee3XzKYEze4Hq4v25ntMyLx1QIJN+Ef0O3EfgweH6SPoW90iSYB7NNdlCMh/EWuB1K9mY5xv3PDGl2xnT26mVifDARbkjpPg1AaZ2FllYI0ezR/4nPzzdmIbh43uxg9jzG2TSlE5VYp8OD9kbcb27 ...28 省略备注:2048位 RSA BEGIN -- END 区间总共约24行29 ...30Uo0fRfEVAoGAK8dO/57YjLGGlJ2+f/yUt8pMN0IFASMJW2BS74+rl6b+KbFfPcXX31AiBtfnH5wG4kuqJYNpOQRuoBpFCpsr8Fgb52gBAM9oRlXj/JbDc+3enTzHe0fCB732DSEIdnl1tHoellxiqFydQpA4ZskAInPmiqcMkBr0UDZY72ffHhClwJ8=33-----END RSA PRIVATE KEY-----34[root@centos openssl_test]# openssl rsa -in genrsa_2048.rsa -pubout35# 将私钥的公钥输出到屏幕36writing RSA key37-----BEGIN PUBLIC KEY-----38MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA3Pemy0XO+3gR7uduvvwp39uiDJjL5UtbzOMee3XzKYEze4Hq4vntMyLx1QIJN+Ef0O3EfgweH6SPoW90iSYB7N40NdlCMh/EWuB1K9mY5xv3PDGl2xnTmVifDARbkjpPg1AaZ2FllYI0ezR/4nPzzdmI41bh43uxg9jzG2TSlE5VYp8OD9kbcbfGEzP4Nemp+0eCkEZkwoG/aHAhQ1hyZAsd91426HJ1FoIXexu9ZzFrZuHbw07ALBnnDq0PC+x3Z0HhsQOOPBn2T9lmKEl0txwDoizY431NyiWWdG58xnhBWLEVLHoiMLaTIXxxtPuiysqOgtRsq/QT7MupOdkQdJjf2EgWEm44uwIDAQAB45-----END PUBLIC KEY-----46
47[root@centos openssl_test]# openssl rsa -in genrsa_2048.rsa -pubout -out genrsa_2048.rsa_public48# 输出公钥到文件49
查看加密私钥文件
xxxxxxxxxx571[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -pubout2# 这个是加密私钥,要求输入密码才能查看公钥、私钥。3Enter pass phrase for genrsa_2048_encrypt.rsa:4writing RSA key5-----BEGIN PUBLIC KEY-----6MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqetgCD6lqGVkd2bUURLP7IFCgeQkMYorY1ezXbshs9tCXgWIWtZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2N8BJ4rwqkpjGTTFSvIVj9z+D13sH6Xq9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfd9zpVKUf6cM44xbgk2nLc7uu5zTs2XJmgiwL4SfD6mY1Kmi+2V7q8g4ktatXzLWCaY108CjJtvAAwIt236W/pSg1o1fJBoeMru/OVYL56C7AcG4JvFwnvS/jK3QjAwGGdsjW11pZr2DTHaBVSCMfNc2PDBAJOWsOb7n9Xwfag2cOTitUU9fOXp4pEVPEFcXB0DV1W+12CwIDAQAB13-----END PUBLIC KEY-----14[root@centos openssl_test]#15
16[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa17Enter pass phrase for genrsa_2048_encrypt.rsa:18writing RSA key19-----BEGIN RSA PRIVATE KEY-----20MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW21tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X22q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X23 ...24 省略备注:2048位 RSA BEGIN -- END 区间总共约24行25 ...26c9ilYO+XCIOZcrjEpTOwLhgf2UIKHxp8a7SVb9c/xnCdL9Bw+YgSP6drnMy8pYmO27frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q28wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM29DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u30-----END RSA PRIVATE KEY-----31[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -pubout -out test_32Enter pass phrase for genrsa_2048_encrypt.rsa:33writing RSA key34[root@centos openssl_test]# ls -alh35total 32K36drwxr-xr-x 2 root root 181 Jul 27 16:50 .37dr-xr-x---. 13 root root 4.0K Jul 27 16:12 ..38-rw-r--r-- 1 root root 963 Jul 27 16:27 genrsa_1024_encrypt.rsa39-rw-r--r-- 1 root root 887 Jul 27 16:23 genrsa_1024.rsa40-rw-r--r-- 1 root root 1.8K Jul 27 16:27 genrsa_2048_encrypt.rsa41-rw-r--r-- 1 root root 1.7K Jul 27 16:43 genrsa_2048.rsa42-rw-r--r-- 1 root root 3.3K Jul 27 16:26 genrsa_4096_encrypt.rsa43-rw-r--r-- 1 root root 3.2K Jul 27 16:19 genrsa_4096.rsa44-rw-r--r-- 1 root root 451 Jul 27 16:50 test_45# 注意公钥的文件大小46[root@centos openssl_test]# cat test_47-----BEGIN PUBLIC KEY-----48MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqetgCD6lqGVkd2bUURLP49IFCgeQkMYorY1ezXbshs9tCXgWIWtZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2N50BJ4rwqkpjGTTFSvIVj9z+D13sH6Xq9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfd51zpVKUf6cM44xbgk2nLc7uu5zTs2XJmgiwL4SfD6mY1Kmi+2V7q8g4ktatXzLWCaY528CjJtvAAwIt236W/pSg1o1fJBoeMru/OVYL56C7AcG4JvFwnvS/jK3QjAwGGdsjW53pZr2DTHaBVSCMfNc2PDBAJOWsOb7n9Xwfag2cOTitUU9fOXp4pEVPEFcXB0DV1W+54CwIDAQAB55-----END PUBLIC KEY-----56[root@centos openssl_test]#57
去除密码
xxxxxxxxxx471[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa2Enter pass phrase for genrsa_2048_encrypt.rsa:3writing RSA key4-----BEGIN RSA PRIVATE KEY-----5MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW6tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X7q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X8 ...9 省略备注:2048位 RSA BEGIN -- END 区间总共约24行10 ...11frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q12wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM13DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u14-----END RSA PRIVATE KEY-----15[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -out xxxx16# 将加密私钥输出17Enter pass phrase for genrsa_2048_encrypt.rsa:18writing RSA key19[root@centos openssl_test]# cat xxxx20-----BEGIN RSA PRIVATE KEY-----21MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW22tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X23q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X24 ...25 省略备注:2048位 RSA BEGIN -- END 区间总共约24行26 ...27c9ilYO+XCIOZcrjEpTOwLhgf2UIKHxp8a7SVb9c/xnCdL9Bw+YgSP6drnMy8pYmO28frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q29wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM30DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u31-----END RSA PRIVATE KEY-----32[root@centos openssl_test]# openssl rsa -in xxxx33# 此时已不要求输入密码34writing RSA key35-----BEGIN RSA PRIVATE KEY-----36MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW37tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X38q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X39 ...40 省略备注:2048位 RSA BEGIN -- END 区间总共约24行41 ...42c9ilYO+XCIOZcrjEpTOwLhgf2UIKHxp8a7SVb9c/xnCdL9Bw+YgSP6drnMy8pYmO43frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q44wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM45DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u46-----END RSA PRIVATE KEY-----47
加密码
xxxxxxxxxx191[root@centos openssl_test]# openssl rsa -in genrsa_2048.rsa -out bbb -des3 -passout pass:abcde2writing RSA key3[root@centos openssl_test]# openssl rsa -in bbb4Enter pass phrase for bbb:abcde5writing RSA key6-----BEGIN RSA PRIVATE KEY-----7MIIEpQIBAAKCAQEA3Pemy0XO+3gR7uduvvwpuiDJjL5UtbzOMee3XzKYEze4Hq4v8ntMyLx1QIJN+Ef0O3EfgweH6SPoW90iSYB7NNdlCMh/EWuB1K9mY5xv3PDGl2xnT9mVifDARbkjpPg1AaZ2FllYI0ezR/4nPzzdmIbh43uxg9jzG2TSlE5VYp8OD9kbcb10 ...11 省略备注:2048位 RSA BEGIN -- END 区间总共约24行12 ...13JgCji3sxh71NwdhfQu2hHCXkA9yLebv/O8QQm6PL3EqWLdn7HAC+weTf5RuXpDAo14Uo0fRfEVAoGAK8dO/57YjLGGlJ2+f/yUt8pMN0IFASMJW2BS74+rl6b+KbFfPcXX15AiBtfnH5wG4kuqJYNpOQRuoBpFCpsr8Fgb52gBAM9oRlXj/JbDc+3enTzHe0fCB716DSEIdnl1tHoellxiqFydQpA4ZskAInPmiqcMkBr0UDZY72ffHhClwJ8=17-----END RSA PRIVATE KEY-----18[root@centos openssl_test]#19
更改密码
-- passin pass:123456 # 密码参数
-des3 -passout pass:abcde # 加密密码参数
输入原密码,参数指定新密码
xxxxxxxxxx231[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -out aaa -des3 -passout pass:abcde2Enter pass phrase for genrsa_2048_encrypt.rsa:3writing RSA key4# 此时要求输入原密码,新密码通过-des3 -passout pass:abcde传入5[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -passin pass:123456 -out aaa -des3 -passout pass:abcde6writing RSA key7[root@centos openssl_test]# openssl rsa -in aaa8# 用新密码打开9Enter pass phrase for aaa:abcde10writing RSA key11-----BEGIN RSA PRIVATE KEY-----12MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW13tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X14q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X15 ...16 省略备注:2048位 RSA BEGIN -- END 区间总共约24行17 ...18c9ilYO+XCIOZcrjEpTOwLhgf2UIKHxp8a7SVb9c/xnCdL9Bw+YgSP6drnMy8pYmO19frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q20wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM21DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u22-----END RSA PRIVATE KEY-----23[root@centos openssl_test]#
仅输入新密码
xxxxxxxxxx61[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -passin pass:123456 -out aaa -des32writing RSA key3Enter PEM pass phrase:4Verifying - Enter PEM pass phrase:5[root@centos openssl_test]#6
同时输入原密码、新密码
xxxxxxxxxx111[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -out aaa -des3 -passout pass:abcde2# 原密码、新密码均通过交互方式输入(新密码有二次确认)3Enter pass phrase for genrsa_2048_encrypt.rsa:4writing RSA key5[root@centos openssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -out aaa -des36Enter pass phrase for genrsa_2048_encrypt.rsa:7writing RSA key8Enter PEM pass phrase:9Verifying - Enter PEM pass phrase:10[root@centos openssl_test]#11
校验文件是否被修改
当然修改后私钥是无效的,无法使用。
xxxxxxxxxx161[root@centos openssl_test]# openssl rsa -in aaa -check2Enter pass phrase for aaa:3RSA key ok # 自校验ok4writing RSA key5-----BEGIN RSA PRIVATE KEY-----6MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW7tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X8q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X9 ...10 省略备注:2048位 RSA BEGIN -- END 区间总共约24行11 ...12c9ilYO+XCIOZcrjEpTOwLhgf2UIKHxp8a7SVb9c/xnCdL9Bw+YgSP6drnMy8pYmO13frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q14wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM15DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u16-----END RSA PRIVATE KEY-----
xxxxxxxxxx211[root@centos openssl_test]# openssl rsa -in aaa -check2Enter pass phrase for aaa:abcde3RSA key error: d e not congruent to 1 # 此时是仅修改了一个字符时的报错。4RSA key error: dmp1 not congruent to d5RSA key error: dmq1 not congruent to d6writing RSA key7-----BEGIN RSA PRIVATE KEY-----8MIIEowIBAAKCAQEAqetgCD6lqGVkd2bUURLPIFCgeQkMYorY1ezXbshs9tCXgWIW9tZsQCeaoWzt2iQ0zt5RDuQHYCkq1kBwvkK2NBJ4rwqkpjGTTFSvIVj9z+D13sH6X10q9ux92o66+cBvqVV+1mTvqSxj4NCWTg1xAfdzpVKUf6cM44xbgk2nLc7uu5zTs2X11 ...12 省略备注:2048位 RSA BEGIN -- END 区间总共约24行13 ...14c9ilYO+XCIOZcrjEpTOwLhgf2UIKHxp8a7SVb9c/xnCdL9Bw+YgSP6drnMy8pYmO15frUVAoGBAISO1QhKMRf+FT7YbV18wjzvBzTa4ne2z96jWbdJMwzlF7cEDP/TE4/q16wgrVXT1B8sYEIUJbhIwJDp6yj0Jrp1808zNHUS40v3EV5M+kOCqoLq3GGgjPpEWM17DBMhmrxDqcAlUzSxGQ61GsMO1XB5bMZHpCNl3Ob8eorTbUs2ok4u18-----END RSA PRIVATE KEY-----19# 其它的报错 20unable to load Private Key21139890935146400:error:0906D066:PEM routines:PEM_read_bio:bad end line:pem_lib.c:802:
speed加密性能测试
测试本机的加密算法的性能(计算能力)
xxxxxxxxxx11# openssl speed [md2] [mdc2] [md5] [hmac] [sha1] [rmd160] [idea-cbc] [rc2-cbc] [rc5-cbc] [bf-cbc] [des-cbc] [des-ede3] [rc4] [rsa512] [rsa1024] [rsa2048] [rsa4096] [dsa512] [dsa1024] [dsa2048] [idea] [rc2] [des] [rsa] [blowfish]大概是10秒多少个:如下
177262/10s
xxxxxxxxxx231[root@centos openssl_test]# openssl speed dsa512 rsa512 rsa20482Doing 512 bit private rsa's for 10s: 177262 512 bit private RSA's in 9.99s3Doing 512 bit public rsa's for 10s: 2101681 512 bit public RSA's in 10.00s4Doing 2048 bit private rsa's for 10s: 8322 2048 bit private RSA's in 10.00s5Doing 2048 bit public rsa's for 10s: 276706 2048 bit public RSA's in 9.99s6Doing 512 bit sign dsa's for 10s: 120092 512 bit DSA signs in 10.00s7Doing 512 bit verify dsa's for 10s: 187931 512 bit DSA verify in 9.99s8OpenSSL 1.0.2k-fips 26 Jan 20179built on: reproducible build, date unspecified10options:bn(64,64) md2(int) rc4(16x,int) des(idx,cisc,16,int) aes(partial) idea(int) blowfish(idx)11compiler: gcc -I. -I.. -I../include -fPIC -DOPENSSL_PIC -DZLIB -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -DKRB5_MIT -m64 -DL_ENDIAN -Wall -O2 -g -pipe -Wall -Wp,-D_FORTIFY_SOURCE=2 -fexceptions -fstack-protector-strong --param=ssp-buffer-size=4 -grecord-gcc-switches -m64 -mtune=generic -Wa,--noexecstack -DPURIFY -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DRC4_ASM -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DWHIRLPOOL_ASM -DGHASH_ASM -DECP_NISTZ256_ASM12 sign verify sign/s verify/s13rsa 512 bits 0.000056s 0.000005s 17743.9 210168.114rsa 2048 bits 0.001202s 0.000036s 832.2 27698.315 sign verify sign/s verify/s16dsa 512 bits 0.000083s 0.000053s 12009.2 18811.917
18
19[root@centos openssl_test]# openssl rand -base64 30;openssl rand -hex 30;openssl rand 30201VwkzoONidGgARKuzxsU1QFco3rVdsSao7olCDcg2150f637130ea027ef5414445d077d78e5ac4fca392b4271a70d7f3278458122▒▒S"▒▒j▒~▒O=▒▒3O▒|▒x▒▒/▒T[root@centos openssl_test]#23
rank生成伪随机数 作密码生成器
xxxxxxxxxx251[root@centos openssl_test]# openssl rand -base64 3038T1vetrHIui9tU/YzC4Owz5FUtS1khSmDFAexIk94[root@centos openssl_test]# openssl rand -hex 30575629487094bbf7ec9a4cee6c96f120afba3366ae61da0a22dc86f2c18a36[root@centos openssl_test]# openssl rand 307R▒▒T▒{▒`)N▒*ν▒▒r▒▒▒78▒▒▒a[root@centos openssl_test]#9[root@centos openssl_test]# openssl rand -rand aaa11Usage: rand [options] num12where options are13-out file - write to file14-engine e - use engine e, possibly a hardware device.15-rand file:file:... - seed PRNG from files16-base64 - base64 encode output17-hex - hex encode output18[root@centos openssl_test]# openssl rand -rand aaa 30191743 semi-random bytes loaded20▒[�▒m▒Q▒▒+Y"U▒f▒u▒▒E_▒[root@centos openssl_test]#21[root@centos openssl_test]# openssl rand -rand aaa -hex 30221743 semi-random bytes loaded235ab338214e42cf4b96a02a54d790dc35040497d01a2c158541e0ad5895f624[root@centos openssl_test]#25
passwd
选项说明:
-crypt:UNIX标准加密算法,此为默认算法。如果加盐(-salt)算密码,只取盐的前2位,2位后面的所有字符都忽略。
-1(数字):基于MD5的算法代号。更多的算法代号见"http://www.cnblogs.com/f-ck-need-u/p/7011460.html#blog222"。
-apr1(数字):apache中使用的备选md5算法代号,不能和"-1"选项一起使用,因为apr1本身就默认了md5。htpasswd工具生成的身份验证密码就是此方法。
-salt:加密时加点盐,可以增加算法的复杂度。但加了盐会有副作用:盐相同,密码相同,加密的结果将一样。
-in file:从文件中读取要计算的密码列表
-stdin:从标准输入中获取要输入的密码
-quiet:生成密码过程中不输出任何信息
xxxxxxxxxx451[root@centos openssl_test]# man sslpasswd # 帮助手册 2[root@centos openssl_test]# openssl passwd 123456;openssl passwd 1234563I4QMiuXObfxQ.4fyuQFqzHk7vrw5
6# 可以看出密码也不一样7# 因为默认使用-crypt是使用随机密码加密的。 可以通过-salt将加密密码固定,但也只取-salt的前2位8[root@centos openssl_test]#9[root@centos openssl_test]# openssl passwd -salt 'xyx' 123456;openssl passwd -salt 'xxx' 12345610xyJkVhXGAZ8tM11xxkVQ7YXT9yoE12# -salt前2位不同,但加密后的值是固定的,就是在不同的主机上执行此命令,都是同样的输出13[root@centos openssl_test]# openssl passwd -salt 'xyx' 123456;openssl passwd -salt 'xyx' 12345614xyJkVhXGAZ8tM15xyJkVhXGAZ8tM16# -salt前2位相同。17[root@centos openssl_test]#openssl passwd -crypt -salt 'xyx' 12345618# 这个是等效完整命令19
20
21# -l 基于md5算法加密密码,同样加-salt参数后,密码将固定,且不限制2位salt。22[root@centos openssl_test]# openssl passwd -1 123456 ; openssl passwd -1 12345623$1$gnQ2oXiZ$5pmHzkczNKejnFvOJ1byT.24$1$547gj6Hu$9/PRvlnk8qHobRA2Ckh/X125[root@centos openssl_test]# openssl passwd -1 123456 ; openssl passwd -1 12345626$1$fhuoZF1N$23aX.Fm/d7VhVGDTzHFoU027$1$bhJ/qMc7$QEu9YaDXXrO3JveGtLB9u/28[root@centos openssl_test]# openssl passwd -1 -salt 'abcde ' 123456 ; openssl passwd -1 -salt 'abcde' 12345629$1$abcde $QfooXY1pJ8YQrb4hqlNFG.30$1$abcde$ZNsM2unwzBdZCr/Y0QzpZ/31[root@centos openssl_test]# openssl passwd -1 -salt 'abcde ' 123456 ; openssl passwd -1 -salt 'abcde' 12345632$1$abcde $QfooXY1pJ8YQrb4hqlNFG.33$1$abcde$ZNsM2unwzBdZCr/Y0QzpZ/34[root@centos openssl_test]# openssl passwd -1 -salt 'abcde ' 123456 ; openssl passwd -1 -salt 'abcde' 12345635$1$abcde $QfooXY1pJ8YQrb4hqlNFG.36$1$abcde$ZNsM2unwzBdZCr/Y0QzpZ/37
38# -apr1 定制版的-l参数,所以就不要同时与-l出现了。39[root@centos openssl_test]# openssl passwd -apr1 123456 ; openssl passwd -apr1 12345640$apr1$x33fWW1u$ueY9aH7EkOMyvx1FfJal2.41$apr1$m7zNn8rw$a2F8W1W0n5MmTf04XIu2M.42[root@centos openssl_test]# openssl passwd -apr1 -salt 'abcde' 123456 ; openssl passwd -apr1 -salt 'abcde' 12345643$apr1$abcde$JfpSak.jThpRLJPtL0SUP044$apr1$abcde$JfpSak.jThpRLJPtL0SUP045
生成sha512密码
xxxxxxxxxx51# grub-crypt --sha-512代替(交互)2python -c 'import crypt,getpass;pw=getpass.getpass();print(crypt.crypt(pw) if (pw==getpass.getpass("Confirm: ")) else exit())'3
4# grub-crypt --sha-512代替(非交互)5python -c 'import crypt,getpass;pw="123456";print(crypt.crypt(pw))'
pkcs12 p12 pfx
pfx (外加了导入密码的二进制文件,iis中常用)<-----> crt+key之间的互转
查看一个通过在线pfx生成网站上制作的文件
windows也认扩展名为p12的导入
xxxxxxxxxx631[root@centos]# openssl pkcs12 -in STAR.zjzwfw.gov.cn_iis.pfx2Enter Import Password: # 提示输入导入密码,没有时可以直接回车。3MAC verified OK4Bag Attributes5 localKeyID: 06 BF 20 14 3B E0 6B FB 48 52 53 D3 32 93 6C CF 57 72 5E A56subject=/C=CN/ST=\xE6\xB5\x99\xE6\xB1\x9F\xE7\x9C\x81/L=\xE6\x9D\xAD\xE5\xB7\x9E\xE5\xB8\x82/O=\xE6\xB5\x99\xE6\xB1\x9F\xE7\x9C\x81\xE4\xBA\xBA\xE6\xB0\x91\xE6\x94\xBF\xE5\xBA\x9C\xE5\x8A\x9E\xE5\x85\xAC\xE5\x8E\x85(\xE6\xB5\x99\xE6\xB1\x9F\xE7\x9C\x81\xE4\xBA\xBA\xE6\xB0\x91\xE6\x94\xBF\xE5\xBA\x9C\xE5\x8F\x82\xE4\xBA\x8B\xE5\xAE\xA4)/OU=\xE4\xBF\xA1\xE6\x81\xAF\xE4\xB8\xAD\xE5\xBF\x83/CN=*.zjzwfw.gov.cn7issuer=/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA8-----BEGIN CERTIFICATE-----9MIIG8DCCBdigAwIBAgIQDZYSfSPTcQMfrDqQX5iL/jANBgkqhkiG9w0BAQsFADBN10MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMScwJQYDVQQDEx5E11aWdpQ2VydCBTSEEyIFNlY3VyZSBTZXJ2ZXIgQ0EwHhcNMjAwNzE0MDAwMDAwWhcN12MjIwOTE0MTIwMDAwWjCBrzELMAkGA1UEBhMCQ04xEjAQBgNVBAgMCea1meaxn+ec13gTESMBAGA1UEBwwJ5p2t5bee5biCMUcwRQYDVQQKDD7mtZnmsZ/nnIHkurrmsJHm14...省略若干行15...16aiHCG2WVYp9zXi19KkootQbZJ9w1Ojno3Axy4IKbhNB1FQfmo+mmR2mK5EbUPEY417bFTwAMFzMFC1s1eI4BJLYdEabg2C5WLrugFMcv+VbrIkXTAO49SXUEnKgZcSUfvd18rkgwyg==19-----END CERTIFICATE-----20Bag Attributes: <No Attributes>21subject=/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA22issuer=/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA23-----BEGIN CERTIFICATE-----24MIIElDCCA3ygAwIBAgIQAf2j627KdciIQ4tyS8+8kTANBgkqhkiG9w0BAQsFADBh25MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB326d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD27QTAeFw0xMzAzMDgxMjAwMDBaFw0yMzAzMDgxMjAwMDBaME0xCzAJBgNVBAYTAlVT28MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxJzAlBgNVBAMTHkRpZ2lDZXJ0IFNIQTIg29U2VjdXJlIFNlcnZlciBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB30ANyuWJBNwcQwFZA1W248ghX1LFy949v/cUP6ZCWA1O4Yok3wZtAKc24RmDYXZK8331nf36QYSvx6+M/hpzTc8zl5CilodTgyu5pnVILR1WN3vaMTIa16yrBvSqXUu3R0bd32...省略若干行33...34xtniMB8GA1UdIwQYMBaAFAPeUDVW0Uy7ZvCj4hsbw5eyPdFVMA0GCSqGSIb3DQEB35CwUAA4IBAQAjPt9L0jFCpbZ+QlwaRMxp0Wi0XUvgBCFsS+JtzLHgl4+mUwnNqipl365TlPHoOlblyYoiQm5vuh7ZPHLgLGTUq/sELfeNqzqPlt/yGFUzZgTHbO7Djc1lGA378MXW5dRNJ2Srm8c+cftIl7gzbckTB+6WohsYFfZcTEDts8Ls/3HB40f/1LkAtDdC382iDJ6m6K7hQGrn2iWZiIqBtvLfTyyRRfJs8sjX7tN8Cp1Tm5gr8ZDOo0rwAhaPit39c+LJMto4JQtV05od8GiG7S5BNO98pVAdvzr508EIDObtHopYJeS4d60tbvVS3bR040j6tJLp07kzQoH3jOlOrHvdPJbRzeXDLz41-----END CERTIFICATE-----42Bag Attributes43 localKeyID: 06 BF 20 14 3B E0 6B FB 48 52 53 D3 32 93 6C CF 57 72 5E A544Key Attributes: <No Attributes>45Enter PEM pass phrase: # 提示输入pem密码这是一个ca+crt+key的三合一文件信息,但指定输出到文件参数时,将输出到屏幕上。46Verifying - Enter PEM pass phrase: # 这个密码是必要输入的,否则不显示或不能导出。47-----BEGIN ENCRYPTED PRIVATE KEY-----48MIIFDjBABgkqhkiG9w0BBQ0wMzAbBgkqhkiG9w0BBQwwDgQIka0ggXMf0yYCAggA49MBQGCCqGSIb3DQMHBAjZAl+FkfCHrASCBMghtLJmiRYSoKMHvXR4eucJQrOc3yK650Ms6/MlRAYeQCJ1h4MWMfACLLx6Bj8gQNveIcNU5EEJZNaq2UwxHpdpQCQqszSr5E51...省略若干行52...53nxo2qbGNTfSEvByHepsG3UoftWiOzV+baiE5k3P7RjEGtyXlqAfWgwjLJ8HWiloc54uTjr5Q0ZV5wYWFXpPDt6OWdnvK+zqwD0XDjqXyeABXGQr+MM0FG+n6FF0vcbF9k455yeLsY+T9LG5egwRYp4SQDVpDb5jWHLJAtYRWX13bvfhDEh40Bd+a24DfU2cCzBuR565ez7fuk9jdkd0V8KGlB6wQPI8PWNAc+yW1njyoVy4PonmL5+oeMej70jsjGMAlAD57bXJsB6me6A0CciLItc49LmT1QfHGTz3/QgXBpWEXnsJIlfvyJxzoKgiezxJKbpyU58aigWrJhZuNmyTOs8B7wDVNRVUC/PV62rz4E435GZNH1pW6dh46UdiTwfxT7X2QNp59eEJrcSnY9nJflv7TPQ96CkUC3r+/zW8vLAh5A0AupwpPcFzij3fgMZ51Z2Ql6JZu60Hek=61-----END ENCRYPTED PRIVATE KEY-----62[root@centos]#63
openssl pkcs12制作转换pfx
xxxxxxxxxx61# 导入的源包括3个文件:ca证书,站点证书,站点证书的key,2# 输出的是pfx3[root@centos]# openssl pkcs12 -inkey site.key -in site_certificate.crt -certfile ca.crt -export -out site_certificate.pfx4Enter Export Password: # 提示输入新创建的文件的导出密码,可以不指定密码。5Verifying - Enter Export Password:6
pfx转pem-->crt key
将PFX文件转换为PEM格式时,OpenSSL会将所有证书和私钥放入一个文件中。您需要在文本编辑器中打开该文件,并将每个证书和私钥(包括BEGIN / END语句)复制到其各自的文本文件中,并将它们分别保存为certificate.cer.crt(域名证书),CACert.cer.crt(根证书,与域名证书类似,可能不包括在其中)和privateKey.key(私钥)。
但其实命令本身的参数也是支持分开导出的(下面有示例),说明它们的生成原理中有一部分就是合并文件。ca证书和网站证书可以合并成一个证书文件,直接复制粘贴合并即可。
...
xxxxxxxxxx791[root@centos]# openssl pkcs12 -in certificate.pfx -out pem_ca_nocerts.crt -nocerts -nomacver -nodes2# 此时仅导出-----BEGIN PRIVATE KEY-----部分,即私钥部分。3Enter Import Password:4[root@centos]# ls -alh5
6-rw-r--r-- 1 root root 1.8K Jul 27 21:08 pem_ca_nocerts.crt7-rw-r--r-- 1 root root 4.5K Jul 27 20:31 STAR.zjzwfw.gov.cn_iis.pfx8[root@centos]# cat pem_ca_nocerts.crt9Bag Attributes10 localKeyID: 98 5F 13 D2 3B A3 76 5F 8C BC 42 C9 64 93 3C 19 C9 74 E1 8A11Key Attributes: <No Attributes>12-----BEGIN PRIVATE KEY-----13MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCt7zCT5ztpf1f714awmFiXW98ajRxGAx6uhQffUeBlA6HjyMMBgzZRGtawUSnPL37TUyk5g1W1i1UyFR15Jo9/iDMuPE7HFdA0S1gm+fsnMO6cYKjATCCGO9HrBg1in+vgVDlvd5A7ryKOa01p16AeWW9IXilTpWtUlrgyYINm2A8+Mpug0MAnyUigy62Mkcktl3Qk4au/+GgESuSuYv17...省略若干行18...19zcwnrW6Dp7xk9dbsNhFhtZnZ4SJR/qMi6DfXPRBUTuiWv0XhyMI3nWL1KIcYQl2d20dgAR85k6qP4xhEhU1QQM2LZ6YWoUVFy/ChFfMmjQ1F+ceYBDYdsz1LI3xb+3nwQb21LWkQieunIZp8Odt+k9GxtfoOjhmOPtB6PHjglt0nAoGAc6FHA4dAURxmyzQY0rno22JjyZ+uLi5WQDyaXGvDitVhBywxQEBpFcEYrF3XdMXpg50lhiOPViOy5+IIeRsvlU236hbRkCzlIEatWcE6pxIDFl3MrqmqqQYyoNme8pp1zxi+8LbCfg/WCmclTBOoieRf24kIE+n0hRYFEMw2Z38fZh0XY=25-----END PRIVATE KEY-----26[root@centos]#27
28# =======================================================================================下面的可用作nginx使用。29
30[root@centos]# openssl pkcs12 -in certificate.pfx -out clcerts.pem -clcerts -nodes31# 此时的pem是包含了client_crt+key的文件,其中的顺序不重要。提取----xxx ----中的段落即可用作nginx使用。32Enter Import Password:33MAC verified OK 输出此处的表明可用。34
35[root@centos]# cat pem_ca_clcerts.crt36Bag Attributes37 localKeyID: 98 5F 13 D2 3B A3 76 5F 8C BC 42 C9 64 93 3C 19 C9 74 E1 8A38subject=/CN=www.haudi.top # 此处为site39issuer=/C=CN/O=TrustAsia Technologies, Inc./OU=Domain Validated SSL/CN=TrustAsia TLS RSA CA40-----BEGIN CERTIFICATE-----41MIIFrDCCBJSgAwIBAgIQDZP6aUi/I3+gAHFZjht6RzANBgkqhkiG9w0BAQsFADBy42MQswCQYDVQQGEwJDTjElMCMGA1UEChMcVHJ1c3RBc2lhIFRlY2hub2xvZ2llcywg43SW5jLjEdMBsGA1UECxMURG9tYWluIFZhbGlkYXRlZCBTU0wxHTAbBgNVBAMTFFRy44...省略若干行45pYi5sZMyK+8+CIvEiooUyQ==46-----END CERTIFICATE-----47-----BEGIN PRIVATE KEY-----48MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCt7zCT5ztpf1f749awmFiXW98ajRxGAx6uhQffUeBlA6HjyMMBgzZRGtawUSnPL37TUyk5g1W1i1UyFR50Jo9/iDMuPE7HFdA0S1gm+fsnMO6cYKjATCCGO9HrBg1in+vgVDlvd5A7ryKOa01p51...省略若干行526hbRkCzlIEatWcE6pxIDFl3MrqmqqQYyoNme8pp1zxi+8LbCfg/WCmclTBOoieRf53kIE+n0hRYFEMw2Z38fZh0XY=54-----END PRIVATE KEY-----55
56
57[root@centos]# openssl pkcs12 -in certificate.pfx -out ca_certs.crt -cacerts -nomacver -nodes58Enter Import Password:59[root@centos]# cat ca_certs.crt60# 此时文件包括 ca + key 但不适合nginx使用61Bag Attributes: <No Attributes>62subject=/C=CN/O=TrustAsia Technologies, Inc./OU=Domain Validated SSL/CN=TrustAsia TLS RSA CA63issuer=/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA64-----BEGIN CERTIFICATE-----65MIIErjCCA5agAwIBAgIQBYAmfwbylVM0jhwYWl7uLjANBgkqhkiG9w0BAQsFADBh66MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB367...省略若干行68pYi5sZMyK+8+CIvEiooUyQ==69-----END CERTIFICATE-----70-----BEGIN PRIVATE KEY-----71MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCt7zCT5ztpf1f772awmFiXW98ajRxGAx6uhQffUeBlA6HjyMMBgzZRGtawUSnPL37TUyk5g1W1i1UyFR73Jo9/iDMuPE7HFdA0S1gm+fsnMO6cYKjATCCGO9HrBg1in+vgVDlvd5A7ryKOa01p74...省略若干行756hbRkCzlIEatWcE6pxIDFl3MrqmqqQYyoNme8pp1zxi+8LbCfg/WCmclTBOoieRf76kIE+n0hRYFEMw2Z38fZh0XY=77-----END PRIVATE KEY-----78
79
只导出ca证书或client certificate证书
xxxxxxxxxx361[root@centos]# openssl pkcs12 -in certificate.pfx -out ca_certs.crt -cacerts -nokeys -nomacver -nodes2Enter Import Password:3[root@centos]# cat ca_certs.crt4Bag Attributes: <No Attributes>5subject=/C=CN/O=TrustAsia Technologies, Inc./OU=Domain Validated SSL/CN=TrustAsia TLS RSA CA6issuer=/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA7-----BEGIN CERTIFICATE-----8MIIErjCCA5agAwIBAgIQBYAmfwbylVM0jhwYWl7uLjANBgkqhkiG9w0BAQsFADBh9MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB310...省略若干行11ISLNdMRiDrXntcImDAiRvkh5GJuH4YCVE6XEntqaNIgGkRwxKSgnU3Id3iuFbW9F12UQ9Qqtb1GX91AJ7i4153TikGgYCdwYkBURD8gSVe8OAco6IfZOYt/TEwii1Ivi1C13qnuUlWpsF1LdQNIdfbW3TSe0BhQa7ifbVIfvPWHYOu3rkg1ZeMo6XRU9B4n5VyJY14RmE=15-----END CERTIFICATE-----16[root@centos]#17
18[root@centos]# openssl pkcs12 -in certificate.pfx -out cl_certs.crt -clcerts -nokeys -nomacver -nodes19Enter Import Password:20[root@centos]# cat cl_certs.crt21Bag Attributes22 localKeyID: 98 5F 13 D2 3B A3 76 5F 8C BC 42 C9 64 93 3C 19 C9 74 E1 8A23subject=/CN=www.haudi.top24issuer=/C=CN/O=TrustAsia Technologies, Inc./OU=Domain Validated SSL/CN=TrustAsia TLS RSA CA25-----BEGIN CERTIFICATE-----26MIIFrDCCBJSgAwIBAgIQDZP6aUi/I3+gAHFZjht6RzANBgkqhkiG9w0BAQsFADBy27MQswCQYDVQQGEwJDTjElMCMGA1UEChMcVHJ1c3RBc2lhIFRlY2hub2xvZ2llcywg28SW5jLjEdMBsGA1UECxMURG9tYWluIFZhbGlkYXRlZCBTU0wxHTAbBgNVBAMTFFRy29dXN0QXNpYSBUTFMgUlNBIENBMB4XDTIwMDcyNzAwMDAwMFoXDTIxMDcyODEyMDAw30MFowGzEZMBcGA1UEAxMQd3d3LnhpbnpoaWJhLnRvcDCCASIwDQYJKoZIhvcNAQEB31...省略若干行32dIe542ikcbJ01yNZT7+XZhMSdclhrBY9xWJ3vEfZN+0NwGnL+8pQWSTA2l2JsRId33pMU+rKpUnytVWMta9Uewfbt8i1vXFyCRv8xdu+AiknpLW2qG2cvE13NiQjWUvPg434pYi5sZMyK+8+CIvEiooUyQ==35-----END CERTIFICATE-----36
pkcs12帮助细节
xxxxxxxxxx501[root@centos]# openssl pkcs12 help2Usage: pkcs12 [options]3where options are4-export output PKCS12 file5-chain add certificate chain6-inkey file private key if not infile7-certfile f add all certs in f8-CApath arg - PEM format directory of CA's9-CAfile arg - PEM format file of CA's10-name "name" use name as friendly name11-caname "nm" use nm as CA friendly name (can be used more than once).12-in infile input filename13-out outfile output filename14-noout don't output anything, just verify.15-nomacver don't verify MAC.16-nocerts don't output certificates.17-clcerts only output client certificates.18-cacerts only output CA certificates.19-nokeys don't output private keys.20-info give info about PKCS#12 structure.21-des encrypt private keys with DES22-des3 encrypt private keys with triple DES (default)23-idea encrypt private keys with idea24-seed encrypt private keys with seed25-aes128, -aes192, -aes25626 encrypt PEM output with cbc aes27-camellia128, -camellia192, -camellia25628 encrypt PEM output with cbc camellia29-nodes don't encrypt private keys30-noiter don't use encryption iteration31-nomaciter don't use MAC iteration32-maciter use MAC iteration33-nomac don't generate MAC34-twopass separate MAC, encryption passwords35-descert encrypt PKCS#12 certificates with triple DES (default RC2-40)36-certpbe alg specify certificate PBE algorithm (default RC2-40)37-keypbe alg specify private key PBE algorithm (default 3DES)38-macalg alg digest algorithm used in MAC (default SHA1)39-keyex set MS key exchange type40-keysig set MS key signature type41-password p set import/export password source42-passin p input file pass phrase source43-passout p output file pass phrase source44-engine e use engine e, possibly a hardware device.45-rand file:file:...46 load the file (or the files in the directory) into47 the random number generator48-CSP name Microsoft CSP name49-LMK Add local machine keyset attribute to private key50
PEM
PEM可以简单的合并ca_certificate.crt / client_certificate.crt / client_certificate.key 来产生,复制粘贴到同一个文件即可。
或者
以此三个文件通过openssl pkcs12 命令输出pfx或p12文件,再由通过命令pfx转换为PEM(建议方案,前文有转换操作)
jks(多用于tomcat)类似于pfx
windows keytools.exe或linux中keytools工具位于jdk中
以下以windows JDK环境测试
xxxxxxxxxx41keytool -import -alias mycert -file d:\site_key.pem -keystore mykeystore.jks2# 有具体帮助。也支持反向转换。3#校验jks证书密钥4keytool -list -v -keystore arbor.jks生成jks
xxxxxxxxxx1961E:\jdk1.8.0_192\bin>keytool.exe --help2密钥和证书管理工具3
4命令:5
6 -certreq 生成证书请求7 -changealias 更改条目的别名8 -delete 删除条目9 -exportcert 导出证书10 -genkeypair 生成密钥对11 -genseckey 生成密钥12 -gencert 根据证书请求生成证书13 -importcert 导入证书或证书链14 -importpass 导入口令15 -importkeystore 从其他密钥库导入一个或所有条目16 -keypasswd 更改条目的密钥口令17 -list 列出密钥库中的条目18 -printcert 打印证书内容19 -printcertreq 打印证书请求的内容20 -printcrl 打印 CRL 文件的内容21 -storepasswd 更改密钥库的存储口令22
23使用 "keytool -command_name -help" 获取 command_name 的用法24
25E:\jdk1.8.0_192\bin>keytool.exe -import -alias mycert -file .\start.pem -keystore mykeystore.jks26输入密钥库口令:27密钥库口令太短 - 至少必须为 6 个字符28输入密钥库口令:29再次输入新口令:30
31E:\jdk1.8.0_192\bin>keytool.exe -import -alias mycert -file .\start.pem -keystore mykeystore.jks32输入密钥库口令: # 定义新的导入密码33再次输入新口令:34所有者: CN=DigiCert SHA2 Secure Server CA, O=DigiCert Inc, C=US35发布者: CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCert Inc, C=US36序列号: 1fda3eb6eca75c888438b724bcfbc9137有效期为 Fri Mar 08 20:00:00 CST 2013 至 Wed Mar 08 20:00:00 CST 202338证书指纹:39 MD5: 34:5E:FF:15:B7:A4:9A:DD:45:1B:65:A7:F4:BD:C6:AE40 SHA1: 1F:B8:6B:11:68:EC:74:31:54:06:2E:8C:9C:C5:B1:71:A4:B7:CC:B441 SHA256: 15:4C:43:3C:49:19:29:C5:EF:68:6E:83:8E:32:36:64:A0:0E:6A:0D:82:2C:CC:95:8F:B4:DA:B0:3E:49:A0:8F42签名算法名称: SHA256withRSA43主体公共密钥算法: 2048 位 RSA 密钥44版本: 345
46扩展:47
48#1: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false49AuthorityInfoAccess [50 [51 accessMethod: ocsp52 accessLocation: URIName: http://ocsp.digicert.com53]54]55
56#2: ObjectId: 2.5.29.35 Criticality=false57AuthorityKeyIdentifier [58KeyIdentifier [590000: 03 DE 50 35 56 D1 4C BB 66 F0 A3 E2 1B 1B C3 97 ..P5V.L.f.......600010: B2 3D D1 55 .=.U61]62]63
64#3: ObjectId: 2.5.29.19 Criticality=true65BasicConstraints:[66 CA:true67 PathLen:068]69
70#4: ObjectId: 2.5.29.31 Criticality=false71CRLDistributionPoints [72 [DistributionPoint:73 [URIName: http://crl3.digicert.com/DigiCertGlobalRootCA.crl]74, DistributionPoint:75 [URIName: http://crl4.digicert.com/DigiCertGlobalRootCA.crl]76]]77
78#5: ObjectId: 2.5.29.32 Criticality=false79CertificatePolicies [80 [CertificatePolicyId: [2.5.29.32.0]81[PolicyQualifierInfo: [82 qualifierID: 1.3.6.1.5.5.7.2.183 qualifier: 0000: 16 1C 68 74 74 70 73 3A 2F 2F 77 77 77 2E 64 69 ..https://www.di840010: 67 69 63 65 72 74 2E 63 6F 6D 2F 43 50 53 gicert.com/CPS85
86]] ]87]88
89#6: ObjectId: 2.5.29.15 Criticality=true90KeyUsage [91 DigitalSignature92 Key_CertSign93 Crl_Sign94]95
96#7: ObjectId: 2.5.29.14 Criticality=false97SubjectKeyIdentifier [98KeyIdentifier [990000: 0F 80 61 1C 82 31 61 D5 2F 28 E7 8D 46 38 B4 2C ..a..1a./(..F8.,1000010: E1 C6 D9 E2 ....101]102]103
104是否信任此证书? [否]: y105证书已添加到密钥库中106
107E:\jdk1.8.0_192\bin>keytool.exe -list -v -keystore mykeystore.jks 108# 此输出与上面生成时的输出一致109输入密钥库口令:110密钥库类型: jks111密钥库提供方: SUN112
113您的密钥库包含 1 个条目114
115别名: mycert116创建日期: 2020-7-27117条目类型: trustedCertEntry118
119所有者: CN=DigiCert SHA2 Secure Server CA, O=DigiCert Inc, C=US120发布者: CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCert Inc, C=US121序列号: 1fda3eb6eca75c888438b724bcfbc91122有效期为 Fri Mar 08 20:00:00 CST 2013 至 Wed Mar 08 20:00:00 CST 2023123证书指纹:124 MD5: 34:5E:FF:15:B7:A4:9A:DD:45:1B:65:A7:F4:BD:C6:AE125 SHA1: 1F:B8:6B:11:68:EC:74:31:54:06:2E:8C:9C:C5:B1:71:A4:B7:CC:B4126 SHA256: 15:4C:43:3C:49:19:29:C5:EF:68:6E:83:8E:32:36:64:A0:0E:6A:0D:82:2C:CC:95:8F:B4:DA:B0:3E:49:A0:8F127签名算法名称: SHA256withRSA128主体公共密钥算法: 2048 位 RSA 密钥129版本: 3130
131扩展:132
133#1: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false134AuthorityInfoAccess [135 [136 accessMethod: ocsp137 accessLocation: URIName: http://ocsp.digicert.com138]139]140
141#2: ObjectId: 2.5.29.35 Criticality=false142AuthorityKeyIdentifier [143KeyIdentifier [1440000: 03 DE 50 35 56 D1 4C BB 66 F0 A3 E2 1B 1B C3 97 ..P5V.L.f.......1450010: B2 3D D1 55 .=.U146]147]148
149#3: ObjectId: 2.5.29.19 Criticality=true150BasicConstraints:[151 CA:true152 PathLen:0153]154
155#4: ObjectId: 2.5.29.31 Criticality=false156CRLDistributionPoints [157 [DistributionPoint:158 [URIName: http://crl3.digicert.com/DigiCertGlobalRootCA.crl]159, DistributionPoint:160 [URIName: http://crl4.digicert.com/DigiCertGlobalRootCA.crl]161]]162
163#5: ObjectId: 2.5.29.32 Criticality=false164CertificatePolicies [165 [CertificatePolicyId: [2.5.29.32.0]166[PolicyQualifierInfo: [167 qualifierID: 1.3.6.1.5.5.7.2.1168 qualifier: 0000: 16 1C 68 74 74 70 73 3A 2F 2F 77 77 77 2E 64 69 ..https://www.di1690010: 67 69 63 65 72 74 2E 63 6F 6D 2F 43 50 53 gicert.com/CPS170
171]] ]172]173
174#6: ObjectId: 2.5.29.15 Criticality=true175KeyUsage [176 DigitalSignature177 Key_CertSign178 Crl_Sign179]180
181#7: ObjectId: 2.5.29.14 Criticality=false182SubjectKeyIdentifier [183KeyIdentifier [1840000: 0F 80 61 1C 82 31 61 D5 2F 28 E7 8D 46 38 B4 2C ..a..1a./(..F8.,1850010: E1 C6 D9 E2 ....186]187]188
189
190
191*******************************************192*******************************************193
194
195
196E:\jdk1.8.0_192\bin>
导出jks为pem
重要的操作是导出其中的key,crt部分是通用的。
支持在线操作,见下方在线链接(需要crt(可以是不完整证书链的证书)+key)。
xxxxxxxxxx111# \jdk\java-1.8.0-openjdk-1.8.0.275-1.b01.dev.redhat.windows.x86_64\bin> .\keytool.exe -v -importkeystore -srckeystore some_domain.jks -destkeystore some_domain.jks.p12 -srcstoretype jks -deststoretype pkcs12 -deststorepass 123456 -destkeypass 1234562正在将密钥库 some_domain.jks 导入到 some_domain.jks.p12...3输入源密钥库口令:4存在现有条目别名 1, 是否覆盖? [否]: y5已成功导入别名 1 的条目。6已完成导入命令: 1 个条目成功导入, 0 个条目失败或取消7[正在存储some_domain.jks.p12]8# openssl pkcs12 -nodes -in some_domain.jks.p12 -out yc.huzhou.gov.cn.jks.p12.key_crt10# 导出时按提示输入密码,然后生成包含key+crt的文本文件,即可自行切割。11
补全证书链
myssl站点支持检测,然后提供在线补全功能。
补全实际上是添加一段ca certificate段,将其与key重新配置到nginx或封装到jks中即可使用。
文件格式与类型
提醒:扩展名不重要,扩展名的使用上,许多平台或个人也命名上没做到可识别。
- .DER .CER,文件是二进制格式,只保存证书,不保存私钥。(windows可打开查看)
- .PEM,一般是文本格式,可保存证书,可保存私钥。
- .CRT,可以是二进制格式,可以是文本格式,与 .DER 格式相同,不保存私钥。(windows可打开查看)
- .PFX .P12,二进制格式,同时包含证书和私钥,一般有密码保护。(windows可打开查看)
- .JKS,二进制格式,同时包含证书和私钥,一般有密码保护。jdk中常用 。
配置实例
yum连接双向认证yum源
xxxxxxxxxx51yum源使用证书认证:自签名证书2需要在客户端服务器安装证书3将证书ca.crt追加到cat ca-key.pem >> /etc/pki/tls/certs/ca-bundle.crt4然后在客户端/etc/hosts中添加对应域名的解析,然后在yum.repo中baseurl中引用域名,而非ip进行调用。
nginx
可以在线生成 https://myssl.com/create_test_cert.html
xxxxxxxxxx31 ssl_certificate /etc/nginx/ssl/server.crt;2 ssl_certificate_key /etc/nginx/ssl/server.key;3 ssl_client_certificate /etc/nginx/ssl/ca.crt; # 非必须xxxxxxxxxx61#公钥2048,生成key及csr2openssl genrsa -out ca.key 20483openssl req -new -subj /C=CN/ST=JS/L=SZ/O=sth/OU=ou/CN=infra/emailAddress=notify2u@163.com -days 36500 -key ca.key -out ca.csr4#sha256位,生成证书5openssl x509 -req -days 36500 -sha256 -signkey ca.key -in ca.csr -out ca.crt6openssl x509 -text -noout -in ca.crt # 查看证书信息
tomcat
xxxxxxxxxx171 <Connector port="443" protocol="org.apache.coyote.http11.Http11Protocol"2 maxThreads="150" SSLEnabled="true" scheme="https" secure="true"3 clientAuth="false" sslProtocol="TLS" keystoreFile="/xxx/xxx/xxx.jks" keystorePass="xxxx" keyAlias="xxxx"/>4
5
6 <Connector port="9443" protocol="HTTP/1.1"7 maxThreads="150" SSLEnabled="true"8 keystoreFile="conf/some.domain.cn.jks" keystorePass="*******" clientAuth="false" sslProtocol="TLS" 9 10 />11 12 或13 <Connector port="9443" protocol="HTTP/1.1"14 maxThreads="150" SSLEnabled="true"15 keystoreFile="/conf/some.domain.cn.jks" keystorePass="*******" clientAuth="false" sslProtocol="TLS" 16 17 />或 ssl单独子标签配置
xxxxxxxxxx71<Connector port="443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true">2 <SSLHostConfig>3 <Certificate certificateKeystoreFile="/xxx/xxx/xxx.jks" certificateKeyAlias="xxx"4 certificateKeystorePassword="xxx"5 type="RSA" />6 </SSLHostConfig>7 </Connector>keystoreFile/certificateKeystoreFile:证书地址,可使用绝对路径,也可以配置相对路径
keyAlias/certificateKeyAlias:生成证书时输入的别名
keystorePass/certificateKeystorePassword:生成证书时输入的密钥
iis证书管理
iis6 (2003)
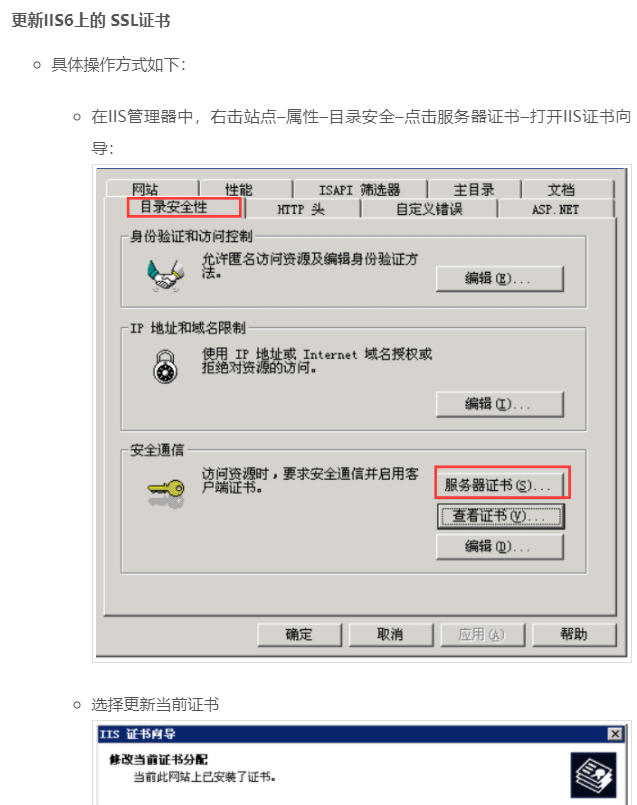
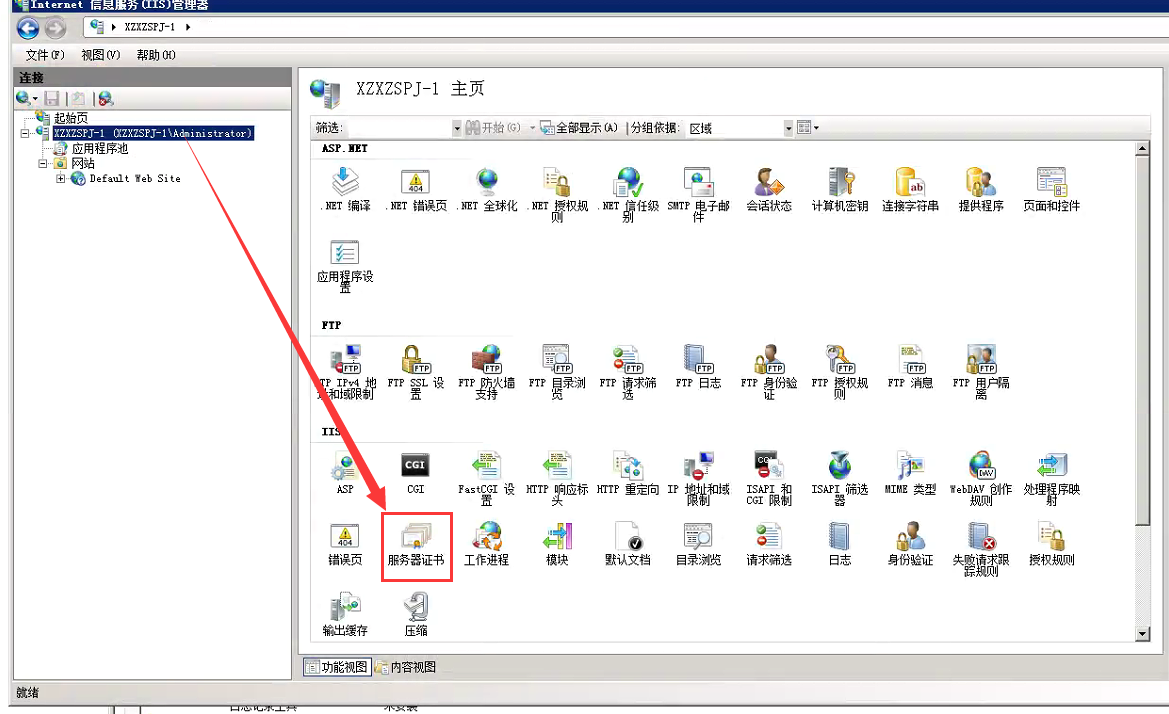
iis7.5(server2008R2)
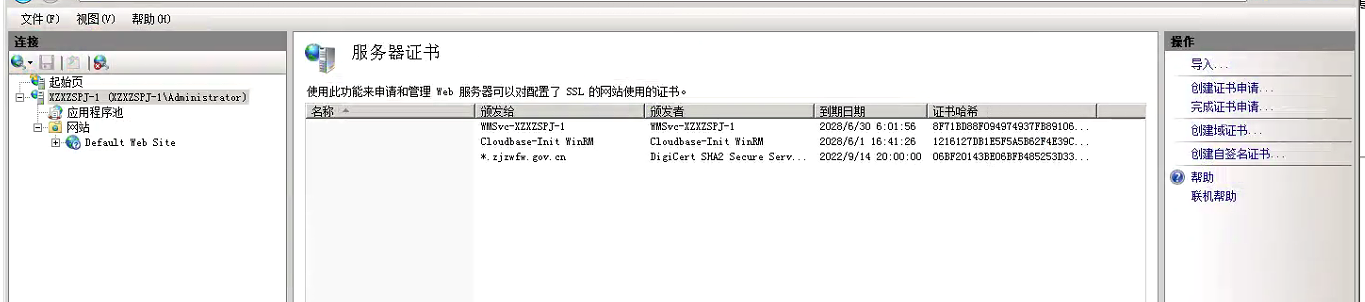
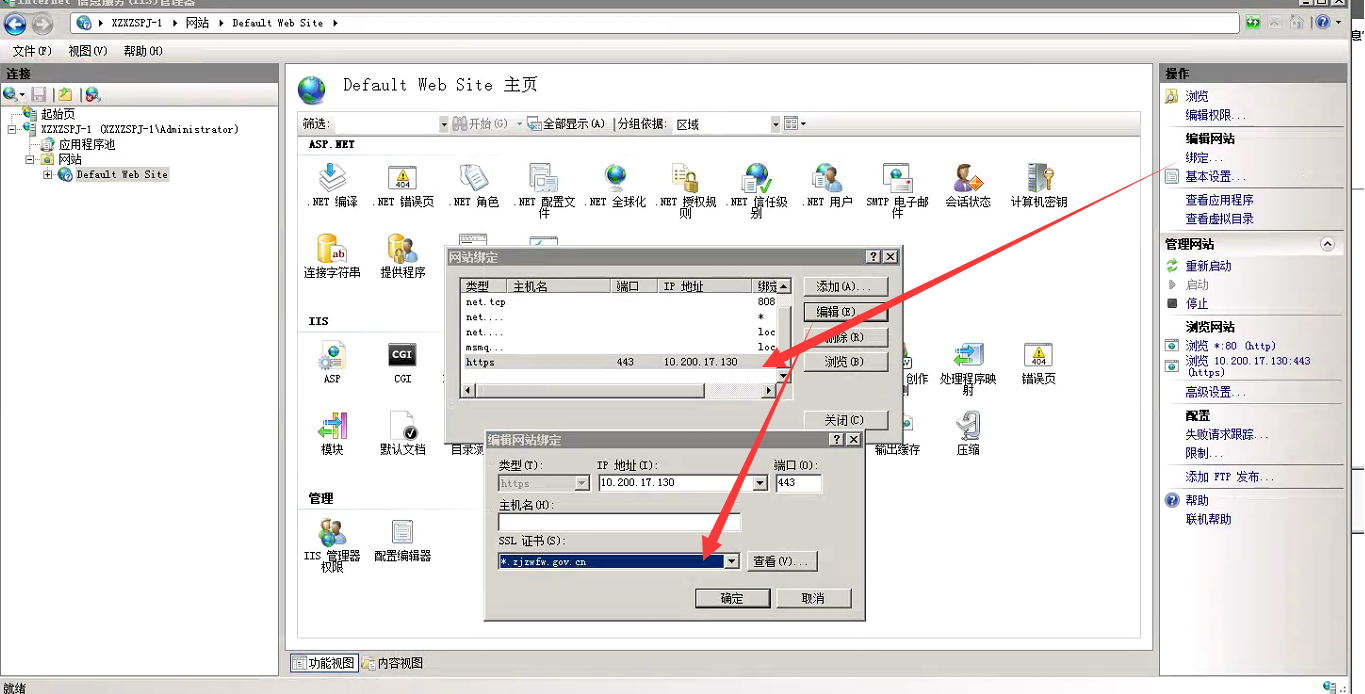
如果有到期的证书,可以先删除,再导入,否则再绑定时,你可能会选错是哪个。
确定后,等待生效。访问地址检查证书是否更新为最新的状态。
x509生成证书
这个是证书的显示效果
xxxxxxxxxx561-----BEGIN CERTIFICATE-----2MIID7jCCAtagAwIBAgIQER6+Jt29QNOQYPVwOT8jVDANBgkqhkiG9w0BAQsFADBe3MQswCQYDVQQGEwJDTjEOMAwGA1UEChMFTXlTU0wxKzApBgNVBAsTIk15U1NMIFRl4c3QgUlNBIC0gRm9yIHRlc3QgdXNlIG9ubHkxEjAQBgNVBAMTCU15U1NMLmNvbTAe5Fw0yMDEyMjgxMTQwMzFaFw0yNTEyMjcxMTQwMzFaMCwxCzAJBgNVBAYTAkNOMR0w6GwYDVQQDExRuaG1zcngubmFuaGFpLmdvdi5jbjCCASIwDQYJKoZIhvcNAQEBBQAD7...省略若干行...83jHp4olXb2pKmrbXdegz5Kg5fBxG7CRkscS9MfDTp8YkAlsmVwyFqyGZR8rpLhqq9N9aZ1GRQ4zZFXM0CeLMPy+OgRYa5t4J0LV5/mcLydBaKvdyYwRUNSpsO9O1pXqNg10eRrXqGmECNZN8lW9ywCVLI+FsnygVKTdwExEGVD69wsfhgQdBM9SM53RLTixCLI611PJ+Rtxuv7css5kQyEZYYov0pkTmIQOK3U6aJfWi/ms9bouDf6v+vbnN3nQhYBvQc12JcA=13-----END CERTIFICATE-----14-----BEGIN RSA PRIVATE KEY-----15MIIEpQIBAAKCAQEA2AKSJCirDjtIBopgixiqs2++Y6ZznQq/4nh+XUlEdQsdBL7i16qqCRYcFwSLQ8q6iUMvq2JhB+zMi7MUxBBxcnaKrDcbIr6nhkD1fElTlSm5TavWfn17Qd1FCLf/EAb6N+jBqwyFuUgAJSWtGo1ekYMKtFiyYyP9Uhv9EfmhRnFoym1ilnTg18hDgV0VCot6z/3YZuDyxeS1lRIRUnvLQDbhDPjcTUPLWtQaL/VDPpllO22CAREYk419aI0GemOLM9vORs6Ls2yJDcwKMhounqQovXKx/EjxxvOwKsecLYi1MnXM66VYcrkO20Me9fs1HcUhFN9PzoeQDRDY+FrjaMDIzRP0VJ9wIDAQABAoIBAQCGGeJ8TDsVlLv821...省略若干行...22JuLR2QmBT70k4FFWxfI0Ps3mqnGbYxmZeUSCGyS/gegHGjNVobjkQJLNDo6CU8WH23Paf1BhDILfCnMMDpgtLzOpN55kqJKVFqDx0NbbOcKHPHSpiEu0gONVIQdOz0rOGj248D2vWWsCgYEAkRp8iqQw/t9BWGthn6h7PNjaajE58Sqc+E7MOsKNY5BxiLbBFeJo25BXEmBIdI5Gqn8JCT45GT2tl5ewO/XXPhQX0oTrya04sLkU793lQUOvPLfdfEusaf26WY3jklogzF6ija05Q4nvoQSKZJLchbfkxXI2BBBrYvqoEUb5whsmFUs=27-----END RSA PRIVATE KEY-----28-----BEGIN CERTIFICATE-----30MIID7jCCAtagAwIBAgIQER6+Jt29QNOQYPVwOT8jVDANBgkqhkiG9w0BAQsFADBe31MQswCQYDVQQGEwJDTjEOMAwGA1UEChMFTXlTU0wxKzApBgNVBAsTIk15U1NMIFRl32c3QgUlNBIC0gRm9yIHRlc3QgdXNlIG9ubHkxEjAQBgNVBAMTCU15U1NMLmNvbTAe33Fw0yMDEyMjgxMTQwMzFaFw0yNTEyMjcxMTQwMzFaMCwxCzAJBgNVBAYTAkNOMR0w34GwYDVQQDExRuaG1zcngubmFuaGFpLmdvdi5jbjCCASIwDQYJKoZIhvcNAQEBBQAD35...省略若干行...363jHp4olXb2pKmrbXdegz5Kg5fBxG7CRkscS9MfDTp8YkAlsmVwyFqyGZR8rpLhqq37N9aZ1GRQ4zZFXM0CeLMPy+OgRYa5t4J0LV5/mcLydBaKvdyYwRUNSpsO9O1pXqNg38eRrXqGmECNZN8lW9ywCVLI+FsnygVKTdwExEGVD69wsfhgQdBM9SM53RLTixCLI639PJ+Rtxuv7css5kQyEZYYov0pkTmIQOK3U6aJfWi/ms9bouDf6v+vbnN3nQhYBvQc40JcA=41-----END CERTIFICATE-----42-----BEGIN CERTIFICATE-----43MIIDuzCCAqOgAwIBAgIQSEIWDPfWTDKZcWNyL2O+fjANBgkqhkiG9w0BAQsFADBf44MQswCQYDVQQGEwJDTjEOMAwGA1UEChMFTXlTU0wxLDAqBgNVBAsTI015U1NMIFRl45c3QgUm9vdCAtIEZvciB0ZXN0IHVzZSBvbmx5MRIwEAYDVQQDEwlNeVNTTC5jb20w46HhcNMTcxMTE2MDUzNTM1WhcNMjcxMTE2MDUzNTM1WjBeMQswCQYDVQQGEwJDTjEO47MAwGA1UEChMFTXlTU0wxKzApBgNVBAsTIk15U1NMIFRlc3QgUlNBIC0gRm9yIHRl48c3QgdXNlIG9ubHkxEjAQBgNVBAMTCU15U1NMLmNvbTCCASIwDQYJKoZIhvcNAQEB49BQADggEPADCCAQoCggEBAMBOtZk0uzdG4dcIIdcAdSSYDbua0Bdd6N6s4hZaCOup50...省略若干行...51648azH/r/GR1S+mXci0Mg6RrDdLzUO7VSf0JULJf98oEPr9fpIZuRTyWcxiP4yh052wVd35OIQBTToLrMOWYWuApU4/YLKvg4A86h577kuYeSsWyf5kk0ngXsL1AFMqjOk53Tc7p8PuW68S5/88Pe+Bq3sAaG3U5rousiTIpoN/osq+GyXisgv5jd2M4YBtl/NlD54ppZs5LAOjct+Aaofhc5rNysonKjkd44K2cgBkbpOMj0dbVNKyL2/2I0zyY1FU2Mk55URUHyMW5Qd5Q9g6Y4sDOIm6It9TF7EjpwMs42R30agcRYzuUsN72ZFBYFJwnBX8=56-----END CERTIFICATE-----
xxxxxxxxxx801C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -text2Certificate:3Data:4Version: 3 (0x2)5Serial Number:611:1e:be:26:dd:bd:40:d3:90:60:f5:70:39:3f:23:547Signature Algorithm: sha256WithRSAEncryption8Issuer: C = CN, O = MySSL, OU = MySSL Test RSA - For test use only, CN = MySSL.com9Validity10Not Before: Dec 28 11:40:31 2020 GMT11Not After : Dec 27 11:40:31 2025 GMT12Subject: C = CN, CN = nhmsrx.nanhai.gov.cn13Subject Public Key Info:14Public Key Algorithm: rsaEncryption15RSA Public-Key: (2048 bit)16Modulus:1700:d8:02:92:24:28:ab:0e:3b:48:06:8a:60:8b:18:18aa:b3:6f:be:63:a6:73:9d:0a:bf:e2:78:7e:5d:49:1944:75:0b:1d:04:be:e2:aa:a0:91:61:c1:70:48:b4:203c:ab:a8:94:32:fa:b6:26:10:7e:cc:c8:bb:31:4c:2141:07:17:27:68:aa:c3:71:b2:2b:ea:78:64:0f:57:22c4:95:39:52:9b:94:da:bd:67:e7:41:dd:45:08:b7:23ff:10:06:fa:37:e8:c1:ab:0c:85:b9:48:00:25:25:24ad:1a:8d:5e:91:83:0a:b4:58:b2:63:23:fd:52:1b:25fd:11:f9:a1:46:71:68:ca:6d:62:96:74:e0:84:38:2615:d1:50:a8:b7:ac:ff:dd:86:6e:0f:2c:5e:4b:59:2751:21:15:27:bc:b4:03:6e:10:cf:8d:c4:d4:3c:b5:28ad:41:a2:ff:54:33:e9:96:53:b6:d8:20:11:11:89:2938:68:8d:06:7a:63:8b:33:db:ce:46:ce:8b:b3:6c:3089:0d:cc:0a:32:1a:2e:9e:a4:28:bd:72:b1:fc:48:31f1:c6:f3:b0:2a:c7:9c:2d:88:b5:32:75:cc:eb:a5:3258:72:b9:0e:31:ef:5f:b3:51:dc:52:11:4d:f4:fc:33e8:79:00:d1:0d:8f:85:ae:36:8c:0c:8c:d1:3f:45:3449:f735Exponent: 65537 (0x10001)36X509v3 extensions:37X509v3 Key Usage: critical38Digital Signature, Key Encipherment39X509v3 Extended Key Usage:40TLS Web Server Authentication, TLS Web Client Authentication41X509v3 Authority Key Identifier:42keyid:28:81:26:05:D1:34:1A:3F:C1:73:0F:BB:93:CF:15:1C:3F:03:BF:7F43Authority Information Access:45OCSP - URI:http://ocsp.myssl.com46CA Issuers - URI:http://ca.myssl.com/myssltestrsa.crt47X509v3 Subject Alternative Name:49DNS:nhmsrx.nanhai.gov.cn50Signature Algorithm: sha256WithRSAEncryption516e:0f:92:1a:7b:1f:67:0d:12:54:af:7a:05:95:10:4d:ed:81:5239:91:a6:34:7d:44:eb:c6:4d:98:fd:06:3d:58:50:09:fd:fb:5371:3e:dc:d8:cf:87:1f:1e:6e:ae:43:3e:17:a1:b7:b2:69:dc:54f7:ec:c3:d5:99:1e:d3:03:de:31:e9:e2:89:57:6f:6a:4a:9a:55b6:d7:75:e8:33:e4:a8:39:7c:1c:46:ec:24:64:b1:c4:bd:31:56f0:d3:a7:c6:24:02:5b:26:57:0c:85:ab:21:99:47:ca:e9:2e:571a:aa:37:d6:99:d4:64:50:e3:36:45:5c:cd:02:78:b3:0f:cb:58e3:a0:45:86:b9:b7:82:74:2d:5e:7f:99:c2:f2:74:16:8a:bd:59dc:98:c1:15:0d:4a:9b:0e:f4:ed:69:5e:a3:60:79:1a:d7:a8:6069:84:08:d6:4d:f2:55:bd:cb:00:95:2c:8f:85:b2:7c:a0:54:61a4:dd:c0:4c:44:19:50:fa:f7:0b:1f:86:04:1d:04:cf:52:33:629d:d1:2d:38:b1:08:b2:3a:3c:9f:91:b7:1b:af:ed:cb:2c:e6:6344:32:11:96:18:a2:fd:29:91:39:88:40:e2:b7:53:a6:89:7d:6468:bf:9a:cf:5b:a2:e0:df:ea:ff:af:6e:73:77:9d:08:58:06:65f4:1c:25:c066-----BEGIN CERTIFICATE-----67MIID7jCCAtagAwIBAgIQER6+Jt29QNOQYPVwOT8jVDANBgkqhkiG9w0BAQsFADBe68MQswCQYDVQQGEwJDTjEOMAwGA1UEChMFTXlTU0wxKzApBgNVBAsTIk15U1NMIFRl69c3QgUlNBIC0gRm9yIHRlc3QgdXNlIG9ubHkxEjAQBgNVBAMTCU15U1NMLmNvbTAe70Fw0yMDEyMjgxMTQwMzFaFw0yNTEyMjcxMTQwMzFaMCwxCzAJBgNVBAYTAkNOMR0w71GwYDVQQDExRuaG1zcngubmFuaGFpLmdvdi5jbjCCASIwDQYJKoZIhvcNAQEBBQAD72...省略若干行...733jHp4olXb2pKmrbXdegz5Kg5fBxG7CRkscS9MfDTp8YkAlsmVwyFqyGZR8rpLhqq74N9aZ1GRQ4zZFXM0CeLMPy+OgRYa5t4J0LV5/mcLydBaKvdyYwRUNSpsO9O1pXqNg75eRrXqGmECNZN8lW9ywCVLI+FsnygVKTdwExEGVD69wsfhgQdBM9SM53RLTixCLI676PJ+Rtxuv7css5kQyEZYYov0pkTmIQOK3U6aJfWi/ms9bouDf6v+vbnN3nQhYBvQc77JcA=78-----END CERTIFICATE-----79C:\Program Files\OpenSSL-Win64\bin>
部分信息输出
xxxxxxxxxx191【信息输出选项:】2-text:以text格式输出证书内容,即以最全格式输出,3:包括public key,signature algorithms,issuer和subject names,serial number以及any trust settings.4-certopt option:自定义要输出的项5-noout :禁止输出证书请求文件中的编码部分6-pubkey :输出证书中的公钥7-modulus :输出证书中公钥模块部分8-serial :输出证书的序列号9-subject :输出证书中的subject10-issuer :输出证书中的issuer,即颁发者的subject11-subject_hash :输出证书中subject的hash码12-issuer_hash :输出证书中issuer(即颁发者的subject)的hash码13-hash :等价于"-subject_hash",但此项是为了向后兼容才提供的选项14-email :输出证书中的email地址,如果有email的话15-startdate :输出证书有效期的起始日期16-enddate :输出证书有效期的终止日期17-dates :输出证书有效期,等价于"startdate+enddate"18-fingerprint :输出指纹摘要信息```19
xxxxxxxxxx261C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -serial2serial=111EBE26DDBD40D39060F570393F23543C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -subject5subject=C = CN, CN = nhmsrx.nanhai.gov.cn6C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -issuer8issuer=C = CN, O = MySSL, OU = MySSL Test RSA - For test use only, CN = MySSL.com9C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -fingerprint11SHA1 Fingerprint=94:16:C4:2F:9D:51:A1:C7:6D:26:C9:E2:76:A5:9F:BE:7A:75:BD:9412C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -issuer_hash14d8b9d49615C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -startdate -enddate17notBefore=Dec 28 11:40:31 2020 GMT18notAfter=Dec 27 11:40:31 2025 GMT19C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -dates21notBefore=Dec 28 11:40:31 2020 GMT22notAfter=Dec 27 11:40:31 2025 GMT23C:\Program Files\OpenSSL-Win64\bin>openssl.exe x509 -in D:\ssl\allinone.txt -noout -email25C:\Program Files\OpenSSL-Win64\bin>
ca签暑选项
x509可以将自身模拟为ca角色,实现证书自签发
xxxxxxxxxx181*****************************************************************************************2* 伪命令x509可以像openssl ca一样对证书或请求执行签名动作。注意,openssl x509 *3* 不读取配置文件,所有的一切配置都由x509自行提供,所以openssl x509像是一个"mini CA" *4*****************************************************************************************5-signkey filename:该选项用于提供自签署时的私钥文件,自签署的输入文件"-in file"的file可以是证书请求文件,也可以是已签署过的证书。-days arg:指定证书有效期限,默认30天。6-x509toreq:将已签署的证书转换回证书请求文件。需要使用"-signkey"选项来传递需要的私钥。7-req:x509工具默认以证书文件做为inputfile(-in file),指定该选项将使得input file的file为证书请求文件。8-set_serial n:指定证书序列号。该选项可以和"-singkey"或"-CA"选项一起使用。9:如果和"-CA"一起使用,则"-CAserial"或"-CAcreateserial"选项指定的serial值将失效。10:序列号可以使用数值或16进制值(0x开头)。也接受负值,但是不建议。11-CA filename :指定签署时所使用的CA证书。该选项一般和"-req"选项一起使用,用于为证书请求文件签署。12-CAkey filename :设置CA签署时使用的私钥文件。如果该选项没有指定,将假定CA私钥已经存在于CA自签名的证书文件中。13-CAserial filename:设置CA使用的序列号文件。当使用"-CA"选项来签名时,它将会使用某个文件中指定的序列号来唯一标识此次签名后的证书文件。14:这个序列号文件的内容仅只有一行,这一行的值为16进制的数字。当某个序列号被使用后,该文件中的序列号将自动增加。15:默认序列号文件以CA证书文件基名加".srl"为后缀命名。如CA证书为"mycert.pem",则默认寻找的序列号文件为"mycert.srl"16-CAcreateserial :当使用该选项时,如果CA使用的序列号文件不存在将自动创建:该文件将包含序列号值"02"并且此次签名后证书文件序列号为1。17:一般如果使用了"-CA"选项而序列号文件不存在将会产生错误"找不到srl文件"。18-extfile filename :指定签名时包含要添加到证书中的扩展项的文件。
流程
xxxxxxxxxx191【CERTIFICATE EXTENSIONS】2-purpose:选项检查证书的扩展项并决定该证书允许用于哪些方面,即证书使用目的范围。3basicConstraints:该扩展项用于决定证书是否可以当作CA证书。格式为basicConstraints=CA:true | false4:1.如果CA的flag设置为true,那么该证书允许作为一个CA证书,即可以颁发下级证书或进行签名;5:2.如果CA的flag设置为false,那么该证书就不能作为CA,不能为下级颁发证书或签名;6:3.所有CA的证书中都必须设置CA的flag为true。7:4.如果basicConstraints扩展项未设置,那么证书被认为可疑的CA,即"possible CA"。8keyUsage:该扩展项用于指定证书额外的使用限制,即也是使用目的的一种表现方式。9:1.如果keyUsage扩展项被指定,那么该证书将又有额外的使用限制。10:2.CA证书文件中必须至少设置keyUsage=keyCertSign。11:3.如果设置了keyUsage扩展项,那么不论是否使用了critical,都将被限制在指定的使用目的purpose上。12例如,使用x509工具自建CA。由于x509无法建立证书请求文件,所以只能使用openssl req来生成请求文件,然后使用x509来自签署。自签署时,使用"-req"选项明确表示输入文件为证书请求文件,否则将默认以为是证书文件,再使用"-signkey"提供自签署时使用的私钥。13[root@xuexi ssl]# openssl req -new -keyout key.pem -out req.csr15[root@xuexi ssl]# openssl x509 -req -in req.csr -signkey key.pem -out x509.crt17x509也可以用来签署他人的证书请求,即为他人颁发证书。注意,为他人颁发证书时,确保serial文件存在,建议使用自动创建的选项"-CAcreateserial"。18[root@xuexi ssl]# openssl x509 -req -in req.csr -CA ca.crt -CAkey ca.key -out x509.crt -CAcreateserial
证书查看
命令查看
xxxxxxxxxx141#查看 PEM - Privacy Enhanced Mail 格式证书文件命令2openssl x509 -in roots.pem -text -noout3***5Validity6Not Before: Sep 1 12:00:00 1998 GMT # 有效期起始与结束。7Not After : Jan 28 12:00:00 2028 GMT8Subject: CN=docs.haudi.top # 对应的域名9DNS:docs.haudi.top10***11
xxxxxxxxxx21#查看 DER - Distinguished Encoding Rules 格式证书命令:2openssl x509 -in roots.der -inform der -text -noout
常识
目前的https用的证书rsa密钥位数一般都是2048位
应用
ssh密钥生成
xxxxxxxxxx51#ssh-keygen -t rsa -b 4096 -f /root/.ssh/new_rsa -N "s3cret" -C "test use only"2# 实现了一次生成密钥对3# openssl rsa 生成过程4# openssl genrsa -out genrsa_2048.rsa 20485# openssl genrsa -out genrsa_2048_encrypt.rsa -des3 -passout pass:123456 2048注意PEM的格式是密钥文本位于一对BEGIN-END之中,但ssh的公钥不是用的这个格式,则需要ssh-keygen从已有的私钥中将公钥输出
xxxxxxxxxx431[root@centos ssl_test]# openssl rsa -in genrsa_2048_encrypt.rsa -passin pass:123456 -pubout -out genrsa_2048.decrypt.pub2writing RSA key3[root@centos ssl_test]# cat genrsa_2048.decrypt.pub4# 此公钥对于ssh来说是不可使用的,私钥的格式是一致的,可以直接使用5-----BEGIN PUBLIC KEY-----6MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAs3Z09BnN8KUjeVbNGIQ27qxoT0fqItBcFDkbPReiE5vQIJw4MOcrCCM86vjwgsfTKkESZncly5WWBmZzPdrN082FlzMl4sXBS0Y+KqOa93cKKmwOzGq+/tjmS3QN7Li+2eSQFpwfpAQd3BLHmKOATs975WqUyBNYPIDaFOjE1bvj3KNE04RR3f7Cb8bjnBxKWpWLt8WTcJ4xnjfafoQwCGi10OAN71NwCt0MIb+8VDmESsE1OQREsd55fhNhZpN9OSPwPFQBC1/kSwBf4J7azjXQ7118c5g/Gs3zxUlV6DBpZrcxxVzBJKJWoE65BazRZsQPbULi7eLHoh16ixveeu5fHNK125wIDAQAB13-----END PUBLIC KEY-----14
15# 转换过程(注意是从私钥输出ssh公钥,不是从公钥输出ssh公钥)16[root@centos ssl_test]# ssh-keygen -y -f genrsa_2048_encrypt.rsa >rsa.pub17@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@18@ WARNING: UNPROTECTED PRIVATE KEY FILE! @19@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@20Permissions 0644 for 'genrsa_2048_encrypt.rsa' are too open.21It is required that your private key files are NOT accessible by others.22This private key will be ignored.23Load key "genrsa_2048_encrypt.rsa": bad permissions # 密钥权限过大不合适24[root@centos ssl_test]# ls -alh25total 12K26drwxr-xr-x 2 root root 83 Jul 28 10:25 .27dr-xr-x---. 13 root root 4.0K Jul 27 16:12 ..28-rw-r--r-- 1 root root 451 Jul 28 10:17 genrsa_2048.decrypt.pub29-rw-r--r-- 1 root root 1.8K Jul 28 10:14 genrsa_2048_encrypt.rsa30-rw-r--r-- 1 root root 0 Jul 28 10:25 rsa.pub31[root@centos ssl_test]# chmod 600 genrsa_2048_encrypt.rsa32# 修改权限仅属主可读写33[root@centos ssl_test]# ssh-keygen -y -f genrsa_2048_encrypt.rsa34Enter passphrase:35ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzdnT0Gc3wpSN5Vs0YhDarGhPR+oi0FwUORs9F6ITm9AgnDgw5ysIIzzq+PCCx9MqQRJmdyXLlZYGZnM92s3TYWXMyXixcFLRj4qo5r3dwoqbA7Mar7+2OZLdA3suL7Z5JAWnB+kBB3cEseYo4BOzvlapTIE1g8gNoU6MTVu+Pco0TThFHd/sJvxuOcHEpalYu3xZNwnjGeN9p+hDAIaI4A3vU3AK3Qwhv7xUOYRKwTU5BESx3nl+E2Fmk305I/A8VAELX+RLAF/gntrONdDvxzmD8azfPFSVXoMGlmtzHFXMEkolagTrkFrNFmxA9tQuLt4seiHXqLG9567l8c0rn36[root@centos ssl_test]# ssh-keygen -y -f genrsa_2048_encrypt.rsa >rsa.pub37# 输入到文件38Enter passphrase:39[root@centos ssl_test]# cat rsa.pub40ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzdnT0Gc3wpSN5Vs0YhDarGhPR+oi0FwUORs9F6ITm9AgnDgw5ysIIzzq+PCCx9MqQRJmdyXLlZYGZnM92s3TYWXMyXixcFLRj4qo5r3dwoqbA7Mar7+2OZLdA3suL7Z5JAWnB+kBB3cEseYo4BOzvlapTIE1g8gNoU6MTVu+Pco0TThFHd/sJvxuOcHEpalYu3xZNwnjGeN9p+hDAIaI4A3vU3AK3Qwhv7xUOYRKwTU5BESx3nl+E2Fmk305I/A8VAELX+RLAF/gntrONdDvxzmD8azfPFSVXoMGlmtzHFXMEkolagTrkFrNFmxA9tQuLt4seiHXqLG9567l8c0rn41
42
43
公钥长库对比
xxxxxxxxxx71# cat .ssh/authorized_keys2# 40963ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCxj+vQv1jow9cVh42M6PHat9nF88vA+Y11EvmXUctebuhFVHa11b3N1fOWMra1RpIJulgUc4JjLRfuJYPri3wTkaPuCHzyFFwQCQPWIOS+YyQAYlE7ACbKENXUgHPHvubdWQT3u5qenauDyZp+JMBbhJ7eUBCuZnZT8eWb7NREPQw3mpMzVatdvToh1eycqWyHzMjhcoG1/nHidcLsqEe+87Dg/TAo/d8W9IGzjZmbELblF2yh91iJ6PTiqbyCcIPJBI8n4dZeOl1NQWpzvfjoz+/ofSTrZxiv6ntgbCKVuz39ygRqeCAZNDphXqPClkPfGDYgcH83SX/nwTh1u+i55HW8bEZCkFssSeAzfxd2p1kYWkR16iOE8sSxsAB10uehIBmk2+ob8bLtLvWgrifDgdpX6KluzoiI0Qtw2C0VOGRD0DM5QR+ELqdCHMHrzPGEEy1EytfcQRmknOnoNe2lJ7f6VQeLCuUc6Mg4h+daSyUg1l3AwD0QU0WnJuASEnZSEemDejLsDeRTPLh0nxm33M6+5NuwVICXtaElbfqjovJ9JBRdXjN8w9Aq1KBOFX6Q7TMNh/3AXJ/Xr+lNGZ05e8JMZziUyPdnpqf7sZ1jYfKDL5XnT67OM8+uUrKhECCSPOPywu7kiRmZhTnSUysrKknnYmCZ/hLV5nHb7VHL+w== imported-openssh-key4
5#20486ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzdnT0Gc3wpSN5Vs0YhDarGhPR+oi0FwUORs9F6ITm9AgnDgw5ysIIzzq+PCCx9MqQRJmdyXLlZYGZnM92s3TYWXMyXixcFLRj4qo5r3dwoqbA7Mar7+2OZLdA3suL7Z5JAWnB+kBB3cEseYo4BOzvlapTIE1g8gNoU6MTVu+Pco0TThFHd/sJvxuOcHEpalYu3xZNwnjGeN9p+hDAIaI4A3vU3AK3Qwhv7xUOYRKwTU5BESx3nl+E2Fmk305I/A8VAELX+RLAF/gntrONdDvxzmD8azfPFSVXoMGlmtzHFXMEkolagTrkFrNFmxA9tQuLt4seiHXqLG9567l8c0rn imported-openssh-key7
rsa类型,命令提示不支持修改注释,rsa1(ssh1版本使用)支持
但是其实可以直接手动在pub文件中修改或添加的。
-t 加密类型
-b 位数
-f 密钥对保存路径(包含公钥+私钥)
-N 私钥口令
-C 公钥注释信息(可以用命令cat查看公钥文件,查看最后的注释,注释可以随意修改)-c -C "new commit"
yum curl 使用
xxxxxxxxxx81系统无法验证证书签发机构问题2curl -i https://www.kzf.com/.well-known/openid-configuration3Peer’s Certificate issuer is not recognized5此种情况多发生在自签名的证书,报错含义是签发证书机构未经认证,无法识别。我们加个 -K 虽然可以解决 但不是根本解决。这个就是缺少中间证书链 ,6解决办法是将签发该证书的私有CA公钥cacert.pem是文件内容,追加到/etc/pki/tls/certs/ca-bundle.crt8如果cacert.pem是关联到自定义域名的,则需要添加对应的域名解析到hosts文件。
网站使用
证书申请后,一般包括以下目录及文件
xxxxxxxxxx181[root@centos scs1594944913408]# tree -L 22.3├── Apache4│ ├── ca.crt5│ ├── server.crt6│ └── server.key7├── IIS8│ ├── keystorePass.txt9│ └── server.pfx10├── Nginx11│ ├── server.crt12│ └── server.key13├── Tomcat14│ ├── keystorePass.txt15│ └── server.jks16└── domain.csr17
xxxxxxxxxx631[root@centos scs1594944913408]# ls -alh2drwxr-xr-x 2 root root 56 Jul 28 11:42 Apache3-rw-r--r-- 1 root root 1.1K Jul 28 10:41 domain.csr4drwxr-xr-x 2 root root 48 Jul 28 11:42 IIS5drwxr-xr-x 2 root root 42 Jul 28 11:42 Nginx6drwxr-xr-x 2 root root 48 Jul 28 11:42 Tomcat7[root@centos scs1594944913408]# ls -alh Nginx/8-rw-r--r-- 1 root root 3.6K Jul 28 10:41 server.crt9-rw-r--r-- 1 root root 1.7K Jul 28 10:41 server.key10[root@centos scs1594944913408]# ls -alh IIS/11-rw-r--r-- 1 root root 16 Jul 28 10:41 keystorePass.txt12-rw-r--r-- 1 root root 4.6K Jul 28 10:41 server.pfx13[root@centos scs1594944913408]# ls -alh Tomcat/14-rw-r--r-- 1 root root 16 Jul 28 10:41 keystorePass.txt15-rw-r--r-- 1 root root 4.0K Jul 28 10:41 server.jks16[root@centos scs1594944913408]# ls -alh a17ls: cannot access a: No such file or directory18[root@centos scs1594944913408]# ls -alh Apache/19-rw-r--r-- 1 root root 1.7K Jul 28 10:41 ca.crt20-rw-r--r-- 1 root root 2.0K Jul 28 10:41 server.crt21-rw-r--r-- 1 root root 1.7K Jul 28 10:41 server.key22[root@centos scs1594944913408]# cat Nginx/server.crt 23# 可对比验证证书关系:Nginx/server.crt = cat Apache/ca.crtcat + Apache/server.crt24# nginx 有最多有两个段,apache是分开的。25-----BEGIN CERTIFICATE-----26MIIFlTCCBH2gAwIBAgIQDuKyL6/4ReKnh7vNZ99x9jANBgkqhkiG9w0BAQsFADBu27MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB328省略20行29RCdCdKeHK0KalvlieleblsU+NjGvF6dE05TUJpRcMog+I1O9dcOzubeWKi1Mw9Ls308DzwdHmu8tsh+33b/QoHplWRxAIWoTGc/eB3hdpzik+lVoBx9x75cb5OnRuu+Qdr31gx8HKuV/ObM+P6UEZ7DANzTj4oLmiIwyEVQxIvijMUwKLg1j1SUWThYln2JeCGun32Q6kQSwCEMF/d1mdMa0HhqMIsit6QENf/ez2LyOJEGEao/sPTZUJHocA=33-----END CERTIFICATE-----34-----BEGIN CERTIFICATE-----35MIIEqjCCA5KgAwIBAgIQAnmsRYvBskWr+YBTzSybsTANBgkqhkiG9w0BAQsFADBh36MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB337省略20行384YSB03Yqp2t3TeZHM9ESfkus74nQyW7pRGezj+TC44xCagCQQOzzNmzEAP2SnCrJ39sNE2DpRVMnL8J6xBRdjmOsC3N6cQuKuRXbzByVBjCqAA8t1L0I+9wXJerLPyErjy40rMKWaBFLmfK/AHNF4ZihwPGOc7w6UHczBZXH5RFzJNnww+WnKuTPI0HfnVH8lg==41-----END CERTIFICATE-----42
43[root@centos scs1594944913408]# cat Apache/server.crt44-----BEGIN CERTIFICATE-----45MIIFlTCCBH2gAwIBAgIQDuKyL6/4ReKnh7vNZ99x9jANBgkqhkiG9w0BAQsFADBu46MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB347省略20行48RCdCdKeHK0KalvlieleblsU+NjGvF6dE05TUJpRcMog+I1O9dcOzubeWKi1Mw9Ls498DzwdHmu8tsh+33b/QoHplWRxAIWoTGc/eB3hdpzik+lVoBx9x75cb5OnRuu+Qdr50gx8HKuV/ObM+P6UEZ7DANzTj4oLmiIwyEVQxIvijMUwKLg1j1SUWThYln2JeCGun51Q6kQSwCEMF/d1mdMa0HhqMIsit6QENf/ez2LyOJEGEao/sPTZUJHocA=52-----END CERTIFICATE-----53[root@centos scs1594944913408]# cat Apache/ca.crt54-----BEGIN CERTIFICATE-----55MIIEqjCCA5KgAwIBAgIQAnmsRYvBskWr+YBTzSybsTANBgkqhkiG9w0BAQsFADBh56MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB357省略20行584YSB03Yqp2t3TeZHM9ESfkus74nQyW7pRGezj+TC44xCagCQQOzzNmzEAP2SnCrJ59sNE2DpRVMnL8J6xBRdjmOsC3N6cQuKuRXbzByVBjCqAA8t1L0I+9wXJerLPyErjy60rMKWaBFLmfK/AHNF4ZihwPGOc7w6UHczBZXH5RFzJNnww+WnKuTPI0HfnVH8lg==61-----END CERTIFICATE-----62[root@centos scs1594944913408]#63
如何在tomcat上安装SSL证书https://support.huaweicloud.com/scm_faq/scm_01_0022.html
如何在Nginx上安装SSL证书https://support.huaweicloud.com/scm_faq/scm_01_0023.html
其它工具导出公钥
puttygen、xshell、securecrt均支持从私钥导出公钥。
比如putty保存的密钥文件(ppk扩展名)是公私在同一个文件中。里面表示了公钥的行数和私钥的行数,但这个是专用的不能用从ppk文本中提取相关行复制粘贴为PEM格式(BEGIN-END对)
xxxxxxxxxx271PuTTY-User-Key-File-2: ssh-rsa2Encryption: none3Comment: rsa-key-202007284Public-Lines: 65AAAAB3NzaC1yc2EAAAABJQAAAQEAji3pW2Q3BsGdt4QUjqP+Um8KmkEOvaIQiAqK6MSvlcBXwyMrMlo15Ap3f9AcjxLZXgWmQTp5tJigLBF8z60lf+340cy6wNI5HHtij7U3Zoi52xTx1Dj93X+offyEdA47TTjhubk1msxpK7lDj/UAGJzD1lEAOawzXkMtel8gK4mKFI6ntmOH0L2yV1GZpLmp2zFk2qSpOC6fwESgUWbtY0Mf+iCzGAC0adfOFH/9vx1GU4QfBKey39Qcr1imS0cWAmt+8ie/9BeQErIcgUwN3ht4k0Q2X9xjO/LHQ4uw10CjmSIKMCBtZOxpcCWYvOIRDmae2+IlKNcK312fCa104IcIIjFw==11Private-Lines: 1412AAABAAPXujLnCGf3ZSCitHKOz4Wv+V4dbxnhyRhu/NDlgr3XFFh0Lwr855hJdMFn13+gw8R43gQiujarvXkZhVmZ6TR8iG3tKuPB0YmiNto4yiVdpCiEBokx+QX8iANnsI142D2BbYBhnGvEJ0OjGdOS1nfIsLJ+MynyQnP6iaCCXmtC+hzD6Vtp68NGgfLpn9am15SLK1ayC9SW1gzYxnVIcmVosKTvdyooC9BIAYKGPgzijNdgpoCBuBDe0GWlsSHAYv16q6AkXdOt+7jh7FTX0NeIzf25xUvZ7uy4KbNiWqSSesFCu+53r2XaK0udZ3EjlF2817tk1t68Rmx4JVrDkey0kZvC7py/0AAACBANeKGuwjQqgvuHYwc5fcUOOJ0A5xGDSy18bqfOsFtOTxiE1KruPmNwXQVTVihFO77aJmlpdTJlE+QuqKaBl35thvB49uNRJDCU19yNN0BHbtdB/QzjtvB9w7Md65lVdRC4zYJ/Teox4LGOcGTovJEBhHDrHnrbNw4CZw20y9dxBwkxABP5AAAAgQCo3m+Ows+GfeC2MBbM9uNmTj7nZMrQgaMzKgq+TsCKN4Jb21Qs/43cyDdX4LlC93+FSJoYt9ONUpVxHy5MvJb6L+4Qt66kw3OrgZ5oHRRM3Uy/Zy22ujaAE4nOwMqayojb0S6zb6ruzb4n+RjQy7p08fv418oEKWvrJ7Fh1Y7Md7eTjwAA23AIBXskj7V2tt5f4VXAin3aN1sSk6nMg2TADCWCHupp0cRX+fPEG/lDQh4JYp1Q8m24ID/UrSHBOt2ofQBoFCwT8ngcPpuYGgmgOpELYcnEDPo+b87Lm6wf5U0dVsPAJXeT25UaTUJBbfGqv+K+Wng3K1+r1jg7A7vL3dPJirdp/n3QMMtw==26Private-MAC: 45dc71e11a4823cbf38b54d0044b798ccc8175cb27
网站https安全等级检测(推荐)
https://myssl.com/haudi.top?status=q
在线生成网站
搜索引擎关键词:ssl证书在线转换
https://myssl.com/create_test_cert.html 先生成,再转换为标准java key storeage。此可以生成自签名证书。
https://www.getssl.cn/export_keystore.php 注意大小 nginx pem4k key2k = jks3k ,另外5k一般不正常。
https://www.myssl.cn/tools/merge-jks-cert.html nginx crt+key 在线转jks(tomcat用)
https://www.myssl.cn/tools/merge-jks-cert.html
https://www.ssleye.com/jks_pkcs12.html
证书相关
https://developer.qiniu.com/fusion/kb/3703/the-certificate-chain-is-what 什么是证书链
xxxxxxxxxx81完整的证书内容一般分为3级,服务端证书-中间证书-根证书,即 end-user certificates, intermediates Certificates 和 root Certificates。2end-user :用来加密传输数据的公钥的证书,是https中使用的证书。开发者牛小七把证书部署在qiniu.com 的服务器上。4intermediates:CA用来认证公钥持有者身份的证书,即确认https使用的end-user证书是属于qiniu.com的证书。5root:用来认证intermediates证书是合法证书的证书。6简单来说,end-user证书上面几级证书都是为了保证end-user证书未被篡改,保证是CA签发的合法证书,进而保证end-user证书中的公钥未被篡改。我们使用end-user certificates来确保加密传输数据的公钥(public key)不被篡改,而又如何确保end-user certificates的合法性呢?这个认证过程跟公钥的认证过程类似,首先获取颁布end-user certificates的CA的证书,然后验证end-user certificates的signature。一般来说,root CAs不会直接颁布end-user certificates的,而是授权给多个二级CA,而二级CA又可以授权给多个三级CA,这些中间的CA就是intermediates CAs,它们才会颁布end-user certificates。7七牛云证书管理,会在用户上传证书的时检测证书的完整性,证书链不完整会自动帮用户补全证书链,但无法保证补全的证书链100%是正确的。所以需要用户选择使用自传的证书还是系统补全后的证书。
refers
xxxxxxxxxx11